John the Ripper - TryHackMe Room
The link for this lab is located here: https://tryhackme.com/room/johntheripper0
In this room, you will learn how to use John the Ripper - an incrediblly powerful and adaptable tool for cracking hashes and passwords
Task 1 - John Who?
A hash is a way of taking a piece of data of any length and representing it in another form that is a fixed length. This masks the original value of the data and is done by running the original data through a hashing algorithm. There are many popular hashing algorithms, such as MD4, MD5, SHA1 and NTLM.
If we were to take the word "polo" - a string of 4 characters and run it through an MD5 hashing algorithm, we end up with an output of b53759f3ce692de7aff1b5779d3964da - a standard 32 character MD5 hash.
Hashing algorithms are designed so that they only operate one way which means a calculated hash cannot be reversed using just the output given. This ties back to a fundamental mathematical problem known as the P vs NP relationship
Abstractly, this means that the algorithm to hash the value will be "NP" and can therefore be calculated reasonably. However, an un-hashing algorithm would be "P" and intractable to solve - meaning that it cannot be computed in a reasonable time using standard computers.
Even though the algorithm itself is not feasibly reversible, that doesn't mean that cracking the hashes is impossible. If you have the hashed version of a password and you know the hashing algorithm, you can use that hashing algorithm to hash a large number of words - a dictionary.
You can then compare these hashes to the one you are trying to crack, to see if any of them match. If they do, you now know what word corresponds to that hash. This process is called a dictionary attack.
Task 3 - Wordlists
In order to perform dictionary attacks against hashes, you need a list of words that you can hash and compare - called a wordlist. There are many different wordlists out there, a good collection to use can be found in the SecLists repository.
For all the tasks in this room, we will use the "rockyou.txt" wordlist which is a very large common password wordlist obtained from a data breach on a website called rockyou.com in 2009.
Task 4 - Cracking Basic Hashes
There are multiple ways to use John the Ripper to crack simple hashes. The basic syntax of JtR is as follows:
john [options] [path to file]
Where:
john - invokes the programs
[path to file] - file containing the hash you are trying to crack
John has built-in features to detect what type of hash it is given and to select appropriate rules and formats to crack it for you. To do this, we use the following syntax:
john --wordlist=[wordlist] [path to file]
Where:
--wordlist=[wordlist] - specifies using wordlist mode and the file
Sometimes John won't automatically recognize hashes. For this, we can use online hash identifiers such as this one or you can use hash-identifier.
Once you have identified the hash you are dealing with, you can tell John to use it while cracking the provided hash using the following syntax:
john --format=[format] --wordlist=[wordlist] [path to file]
Where:
--format=[format] - tells John what format the hash is in
When you are telling John to use formats, if you are dealing with a standard hash type (eg. MD5) you have to prefix it with "raw-" to tell John you are just dealing with a standard hash type.
To check if you need to add the prefix or not, you can list all of John's formats using "john --list=formats" and either check manually or grep for your hash type using something like "john --list=formats" | grep -iF "md5".
Questions
Q1: What type of hash is hash1.txt?
A: Using an online hash identifier, we can see that it appears as an MD5 hash
Q2: What is the cracked value of hash1.txt?
A: Using the format of raw-md5 for john and the wordlist of rockyou.txt, we get the answer - biscuit
Q3: What type of hash is hash2.txt?
A: Using an online hash identifier, we can see that it appears as a SHA1 hash
Q4: What is the cracked value of hash2.txt?
A: Using the format of raw-sha1 for john and the wordlist of rockyou.txt, we get the answer - kangeroo
Q5: What type of hash is hash3.txt?
A: Using an online hash identifier, we can see that it appear as a SHA256 hash
Q6: What is the cracked value of hash3.txt?
A: Using the format of raw-sha256 for john and the wordlist of rockyou.txt, we get the answer - microphone
Q7: What type of hash is hash4.txt?
A: Using an online hash identifier, we can see that it appear as a Whirlpool hash
Q8: What is the cracked value of hash4.txt?
A: Using the format of whirlpool for john and the wordlist of rockyou.txt, we get the answer - colossal
Task 5 - Cracking Windows Authentication Hashes
Authentication hashes are the hashed versions of passwords that are stored by operating systems. It is sometimes possible to crack them using the brute-force methods. To get your hands on these hashes, you must often already be a privileged user.
NTHash is the hash format that modern Windows OS machines will store user and service passwords in. It is also commonly referred to as "NTLM" which references the previous version of Windows format for hashing passwords known as "LM" thus "NT/LM".
You can acquire NTHash/NTLM hashes by dumping the SAM database on a Windows machine by using a tool like Mimikatz or from the Active Directory database - NTDS.dit. You may not have to crack the hash to continue privilege escalation if you can perform a "pass the hash" attack but sometimes cracking the hash is a viable option if there is a weak password policy.
Questions
Q1: What do we need to set the format flag to in order to crack this?
A: Listing the formats in john and grepping for "ntlm" - sudo john --list=formats | grep -iF ntlm - reveals one that matches what we just learned
Q2: What is the cracked value of this password?
A: Using the syntax of "--format=nt" and the rockyou.txt wordlist reveals the password - mushroom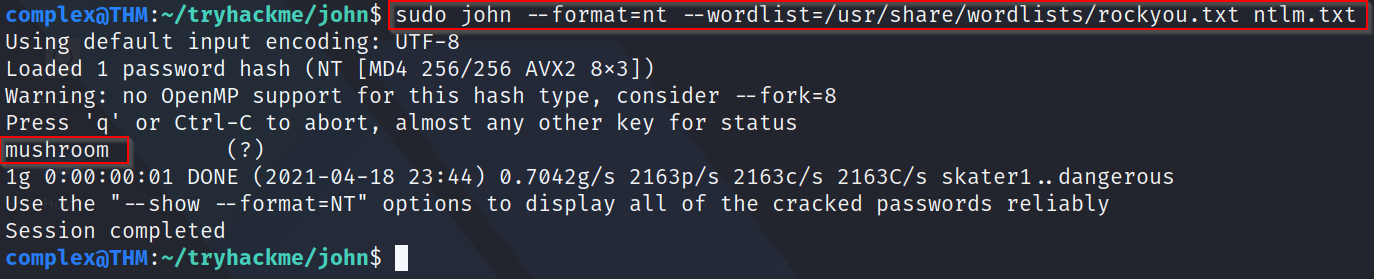
Task 6 - Cracking /etc/shadow Hashes
The "/etc/shadow" file is the file on Linux machines where password hashes are stored. It also stores other information such as the date of last password change and password expiration information. It contains one entry per line for each user or user account of the system. This file is usually only accessible by root.
John can be very particular about the formats it needs data in to be able to work with it. For this reason, in order to crack /etc/shadow passwords, you must combine it with the /etc/passwd file in order for John to understand the data it is being given. To do this, we use a tool called "unshadow". The syntax is as follows:
unshadow [passwd file] [shadow file]
Where:
unshadow - command
[passwd file] - passwd file from target
[shadow file] - shadow file from target
When using unshadow, you can either use the entire /etc/passwd and /etc/shadow files or you can use the relevant line from each.
Once finished, we are then able to feed the output from unshadow directly into John. We should not need to specify a mode as we made the input specifically for John. In some cases, you will need to specfiy the format.
Questions
Q1: What is the root password?
A: Using the "sha512crypt" format and the rockyou.txt wordlist reveals the password - 1234
Task 7 - Single Crack Mode
John has another mode called "Single Crack". In this mode, John uses only the information provided in the username, to try and work out possible passwords heuristically, by slightly changing the letters and numbers contained within the username.
The best way to show what Single Crack mode is and what it does, is to go through an example. If we take the username "Markus" some possible passwords could be:
Markus1, Markus2, Markus3 etc...
MArkus, MARkus, MARKus etc…
Markus!, Markus$, Markus* etc…
This technique is called word mangling. John is building it's own dictionary based on the information it has been fed and uses a set of rules called mangling rules which define how it can mutate the word it started with to generate a wordlist based off of relevant factors for the target you are trying to crack.
This is exploiting how poor passwords can be based off of information about the username or the service they are logging into.
John's implementation of word mangling also features compatibility with the GECOS fields of the UNIX OS and other UNIX-like operating systems such as Linux.
Each one of the fields in the passwd and shadow file are seperated by colons. These fields are called GECOS fields. John can take information stored in those records such as full name and home directory name to add in to the wordlist it generates when cracking shadow hashes with single crack mode.
To use single crack mode, we use roughly the same syntax except adding the "--single" parameter to John:
john --single --format=[format] [path to file]
Where:
--single - tells John you want to use single hash cracking mode
If you are cracking hashes in single crack mode, you need to change the file format that you are feeding John for it to understand what data to create a wordlist from. You do this by prepending the hash with the username that the hash belongs to:
mike:[hash]
Questions
Q1: What is Joker's password?
A: Using the username of "Joker", we first append the username to the start of the hash provided
Next, we need to identify what type of hash it is. Using an online identifier, we see it is MD5.

Then, we use John with the "--single" parameter and the format of raw-md5 to find the password - Jok3r.

Task 8 - Custom Rules
Many organizations will required a certain level of password complexity to try and combat dictionary attacks. Things like capital letters, numbers and symbols may be required for passwords. We can exploit the fact that most users will be predictable in the location of these symbols.
A password with the capital letter first, and a number followed by a symbol at the end. This pattern of the familiar password, appended and prepended by modifiers is a memorable pattern that people use and reuse.
Custom rules are defined in the "john.conf" file usually located in "/etc/john/john.conf".
The first line in this file is as follows:
[List.Rules:THMRules] - used to define the name of your rule
We then use a regex style pattern match to define where in the word will be modified:
Az - takes the word and appends it with the characters you define
A0 - takes the word and prepends it with the characters you define
c - capitalized the character positionally
These can be used in combination to define where and what in the word you want to modify. Lastly, we need to define what characters should be appended, prepended or otherwise included. We do this by adding character sets in square brackets [] in the order they should be used. These directly follow the modifier patterns inside of double quotes "". Some common examples are:
[0-9] - include numberse 0-9
[0] - only include number 0
[A-z] - both uppercase and lowercase
[A-Z] - only uppercase
[a-z] - only lowercase
[a] - only single letter a
[!£$%@] - include these symbols
Putting all this together, in order to generate a wordlist from the rules that would match the example password "Polopassword1!", we would create a rule entry that looks like this:
[List.Rules:PoloPassword]
cAz"[0-9] [!£$%@]"
This will:
Capitalize the first letter - c
Append to the end of the word - Az
A number in the range 0-9 - [0-9]
Followed by a symbol - [!£$%@]
We could then call this custom rule as a John argument using the "--rule=PoloPassword" flag. As a full command, this would look like:
john --wordlist=[wordlist] --rule=PoloPassword [path to file]
Questions
Q1: What do custom rules allow us to exploit?
A: Password complexity predictabilityQ2: What rule would we use to add all capital letters to the end of a word?
A: Az"[A-Z]"Q3: What flag would we use to call a custom rule calle "THMRules"?
A: --rule=THMRulesTask 9 - Cracking Password Protected ZIP Files
We can also use John to crack the password on password protected Zip files. Similiarly to the unshadow tool, we use "zip2john" tool to convert the zip file into a hash format that John is able to understand, and hopefully crack. The basic usage is as follows:
zip2john [options] [zip file] > [output file]
Where:
[options] - allows you to pass specific checksum options to zip2john
[zip file] - zip file to get hash of
> [output file] - send output to a file
Once done, we are then able to take the file we output from zip2john and feed it directly into John as we have made the input specifically for it.
Questions
Q1: What is the password for the secure.zip file?
A: First, we have to convert it using zip2john and put it into a text file.
Next, we simply crack the password using rockyou to get the password - pass123

Q2: What is the contents of the flag inside the zip file?
A: We simply enter the password when extracting the ZIP contents to reveal the flag
Task 10 - Cracking Password Protected RAR Archives
We can use a simiiar process to the one we used in the last task to obtain the password for rar archives. RAR archives are compressed files created by the Winrar archive manager.
Almost identical to the zip2john tool, we can use the rar2john tool to convert the rar file into a hash format that John is able to understand. Once again the syntax is as follows:
rar2john [rar file] > [output file]
Once again, we are then able to take the file we output from rar2john and feed it directly into John.
Questions
Q1: What is the password for the secure.rar file?
A: First, we use the rar2john tool to output it into a file and then we use the rockyou wordlist to find the password - password
Q2: What is the contents of the flag inside the zip file?
A: First, to uncompress the RAR file, we need to use the "unrar e [file]" command to extract the contents. Then, we simply cat out the flag.txt file
Task 11 - Cracking SSH Keys with John
Using John to crack the SSH private key password of id_rsa files. Unless configured otherwise, you authenticate your SSH login using a password. However, you can configure key-based authentication which lets you use your private key as an authentication key to login to a remote machine over SSH.
However, doing so will often require a password which we can crack.
The ssh2john tool converts the id_rsa private key that you use to login to the SSH session into a hash format that John can work with. The syntax is very similiar:
ssh2john [id_rsa key file] > [output file]
Then, we simply feed it to John to crack.
Questions
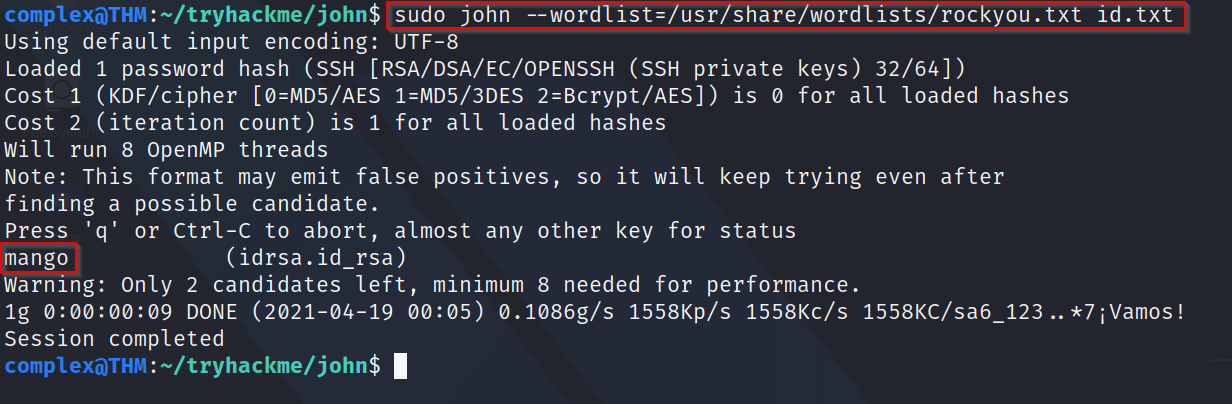
Q1: What is the SSH private key password?
A: First, we convert the id_rsa key to a text file using ssh2john
Then, we simple crack it using John to reveal the password - mango
Task 12 - Further Reading
If you want more information about John, you can check out the Openwall Wiki here for more information











