Introduction to Industrial Control Systems
In Part 4 of this new Cyber Physical Systems series, I will introduce the concept of industrial control systems along with their components and different types of ICS.
Introduction to Industrial Control Systems
An Industrial Control System (ICS) is a control system that is designed for use in an industrial environment. It performs several actions such as logic, sequencing, timing, counting, and arithmetic to control multiple machines and/or processes.
These actions are performed by sensing the environment through their inputs and generating appropriate signals on their output.
A key difference between ICS and IT is that ICS always interact with the physical environment. Traditionally, securing critical infrastructure systems involved safety and reliability, and to develop the appropriate techniques for fault detection, isolation and recovery.
In CPSs, however, the additional cyber element introduces vulnerabilities which are not directly addressed. ICS also requires the cyber element to be secured.
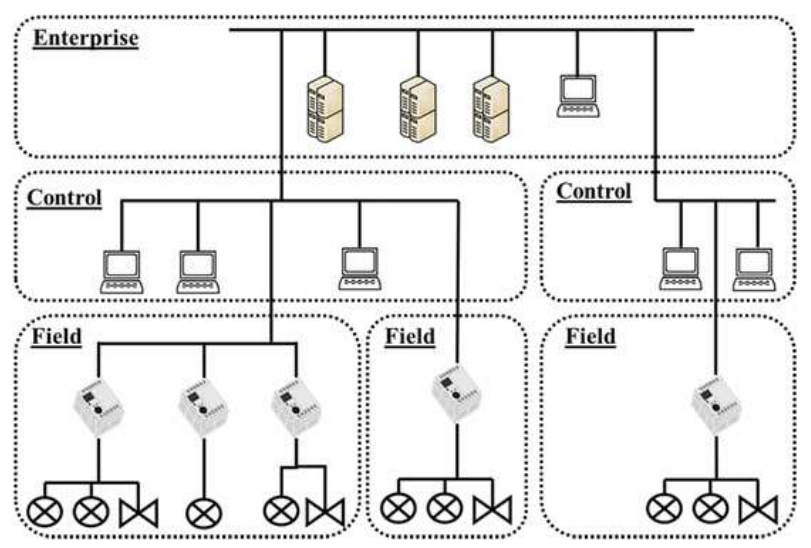
ICS can be very complex and vast (geographically distributed). For simplicity, ICS is divided into three operational zones:
Enterprise zones - business networks and enterprise systems. Internet Protocol (IP) is quite common. All IT security solutions can be applied here.
Control zones - real-time control elements in SCADA (Suerpvisory Control and Data Acquisition) systems. Usually IP. Devices in this zone may not be updated as often. Few cybersecurity solutions can be applied here. Devices here usually last decades. Not generally built for updates/remote patches.
Field zone or (plant/process/operation-zone) - devices and networks in charge of control and automation. It hosts the CPSs. Devices in this zone have embedded devices, programmable logic control (PLC). Variety of protocols including IP. Has lots of different proprietary protocols. IT solutions are rarely applicable.
In the image above, it simplifies the 3 zones. For a more detailed example, we can look at the following.
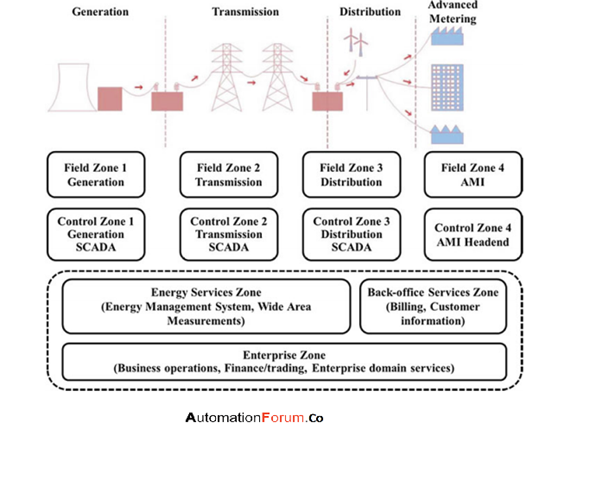
Looking at the smart grid, it can be far more complex. You are dealing with a distributed ICS - not everything is on one side. For example, you have the generation of the power, then the transmission across these towers and wires, then to something like a power box which then distributes it to clients/buildings/houses/etc....
Additionally, there are multiple field zones for each part of the pipeline and each would have their own control zone. Above that, in the enterprise zone, it could be that there is only one centralized zone that collects data from all the systems and managing control over the regions.
It's a very simplified breakdown of a large ICS, but it gives an easy example to understand the different zones.
Field systems are real-time - they interact with its environment, continuously accepting requests from the environment and continuously producing reactions). Devices in the field zone often work in real time, taking measurements. Based on those measurements, if they receive any reactions, they will execute those reactions.
Field systems also have stringent requirements in terms of reliability and safety - IMPORTANT. Additionally, they are usually implemented with severe resource constraints (very limited processing power, limited energy resources). They also often rely on legacy platforms that are not updated or patched, and typically use proprietary communication protocols, making it difficult to make it secure.
With these constraints, there is a lack of antivirus software for embedded systems. They have no OS, limited computational power meaning they lack stuff like IDS, firewalls, antivirus etc...
A good short video to watch for more information on general ICS can be found below:
Three ICS Security Misconceptions
Three of the main ICS misconceptions in terms of security are:
Air Gap Security - with an air gap, it provides security. If it's not connected to the internet, it is safe from vulnerabilities and attacks. This is not correct. It is possible to breach the airgap over time (i.e. USB being plugged in). It won't exist forever.
Security through obscurity - control systems use proprietary protocols that no one knows about. This is again an issue of time. Attackers can do research and reconnaissance. Once they do this research, the legacy software problem comes into play. Since they cannot be upgraded or patched, it is just a matter of time until a vulnerability is found.
You can use standard IT security - ICS personnel need to follow the IT security practices. Network scans like Nmap can crash and interrupt the legacy devices which in terms of ICS is very, very bad. Automatic updates can break critical functionality and IT security products usually don't understand ICS protocols like Modbus.
If you want to understand a little more, you can see a list of advisories for different make and model of ICS devices - https://www.cisa.gov/uscert/ics/advisories
Purdue Model
Developed in the 1990s by Theodore J. Williams and members of the Purdue University, the Purdue model is a structural model for ICS security, concerning physical processes, sensors, supervisory control, operations and logistics.
It defines the different levels of critical infrastructure used in production lines and how to secure them. When it was introduced, it was ahead of its time and, implemented correctly, could have achieved the air gap between ICS or OT and IT systems.
In essence, it is similiar to the TCP/IP or OSI model, but is designed for ICS security:
There are different interpretations. Another one is:
And many more!
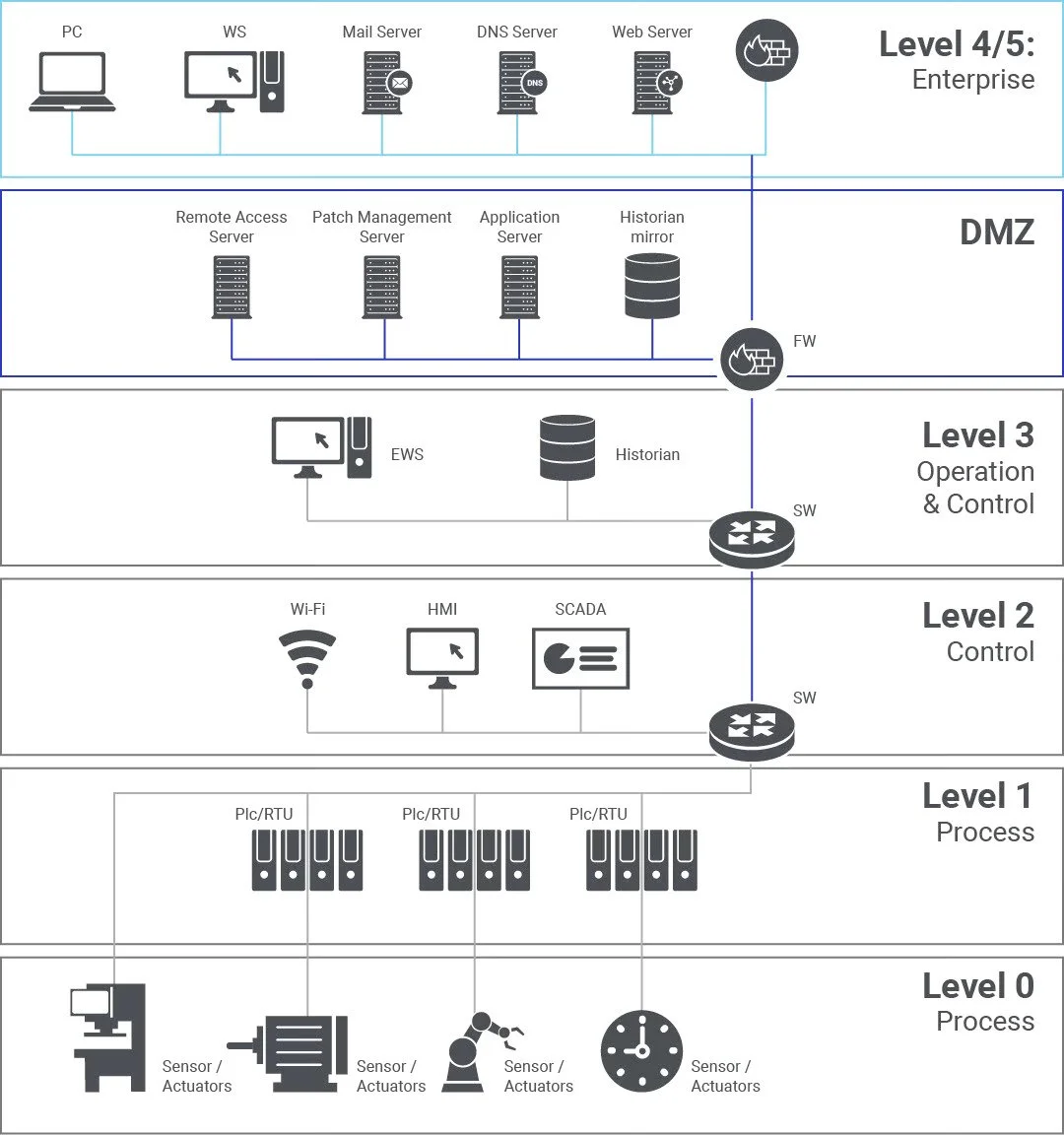
Digging into more detail about the levels, we can start with Levels 4 & 5 - the Enterprise level.
Levels 4 & 5 are typically the IT network where the primary business functions occur. The levels provide business direction and orchestrates manufacturing operations. Enterprise resource planning (ERP) systems drive plant production schedules, material use, shipping, and inventory levels.
Popular ERP systems include offerings from Oracle, SAP, Microsoft and Epicor. Any disruptions at this level can lead to days or even weeks of downtime, creating the potential for significant revenue loss with downstream processes delayed or stopped.
Some examples of things at these leveles can be things like:
Core business services
Email
Management
Billing
Customer service
Remote access to the IT network
Managed by IT personnel
Going even further, you can break down these two layers separately into the following. Level 5 can be called the Enterprise Network Layer and Layer 4 can be the Business Network Layer.
In Layer 5, this includes the corporate-level services supporting individual business units and users. These systems are usually located in corporate data centers and includes providing things like Active Directory, internal emails, HR systems, backup solutions, etc...
In Layer 4, this can be more of the IT network side for businesses. Connectivity to enterprise wide area network (WAN) and possibly local internet access would be at this level. Direct internet access should not extend below this level (in an ideal world). Some things at this level can include workstations, local phone systems, print servers, etc...
Going further down, Layer 3 is where the monitoring, supervisory and operational support for a site comes in. With this, you get stuff like management servers, HMIs, alarm servers, analytic systems - more of the nitty-gritty systems rather than the high level systems.
Layer 2 is more monitoring and supervisory control but is typically for a single process, cell, line or distributed control system solution. It typically isolates processes from one another, grouping by function, type or risk. The same items exist in this layer (management servers, HMIs, etc..)
Layer 1 gets to the dirty devices. These are the devices/systems that provide automated control of a process, cell, line or DCS solution. Modern ICS solutions often combine levels 1 and 0. In this level, you'll find PLCs, control processors, RTUs, process-specific microcontrollers, etc....
Just to cover Layer 0 on its own, this is more or less the sensors/actuators/valves that do the work. It includes things like basic sensors and actuators, IEDs, IIoT devices, communications gateways and other field instrumentation.
Generally speaking, as you move down the hierarchy, devices have more access to critical processes, but fewer intrinsic security capabilities.
If you want more information, SANS cover this topic in depth:
European Union Agency for Cybersecurity
ENISA has a revised version of the Purdue model:
I won't keep boring you with the details of models over and over, but if you want a deeper look at this particular model, I recommend reading the following link.
Industrial Control System Components
There are elements in the ICS and attacks can begin at an ICS element, targeting some of the other elements. That is why ALL elements of ICS need to be studied. These components include:
Programmable Logic Controller (PLC)
Remote Terminal Unit (RTU)
Intelligent Electronic Device (IED)
Engineering Workstation (EWS)
Human Machine Interface (HMI)
Data historian
Communication gateway
Front end processor
Field devices
Before going into detail about each one, we need to cover some background knowledge.
First, a relay or actuator is similiar to a switch, except it is not controlled with direct mechanical interaction, but rather controlled by an electrical signal/pulse/voltage. A good video can be found here:
They are similiar to transistors. In fact, there are solid state relays as well that do not have any moving part.
An example - think of your smart plug/lights. You can shout at Alexa to turn them on/off. Or even an oven - you set the temperature and there is a small controller inside that senses the temperature and activates the relay which turns on the heating element to cook your food. All of these are controlled by small electrical signals/pulses.
Relays are controlled (switched on/off) by a small voltage that is generated by the PLC. Once a relay is on, it can power much more powerful devices such as the electric oven.
Mechanical magnetic relays make clicking noises when they switch. However, solid state relays do not make any noise as they have no moving mechanical parts. An example of a relay can be found in this video:
Programmable Logic Controller (PLC)
PLCs are the brains of the ICSs. A PLC is a specialized computer (microprocessor-based controller, or microcontroller) that performs the logic for controlling the machines and processes.
A PLC reads input signals from sensors, executes programmed instructions using these inputs as well as orders from supervisory controllers, and create output signals which may change/switch or move actuators.
A PLC is the first type of ICS controller and is the boundary between the cyber world and the real-world. The PLC has revolutionized how controlling functions are implemented. They allowed the logic to be implemented using software through the use of relays (electrical switches).
IEC-1131 standards for PLCs was introduced around 1993. It introduced standards so programmers can develop a control algorithm (referred to as a project) using any combination of five control languages. The current standard is IEC-61131.
The control algorithm can include reusable entities referred to as "program organization units (POUs)" which include Functions, Function Blocks, and Programs. The IEC-1131 standard includes a library of pre-programmed functions and function blocks.
Any controller that is IEC compliant supports these as a "firmware" library, that is, the code for these is pre-written into a flash RAM on the device.
The IEC-1131 standardized 5 languages for PLC programming are:
Instruction List (IL) - assembler-style language
Structured Text (ST) - high-level language
Ladder Diagram (LD) - electrical technician's language
Function Block Diagram (FBD) - graphical language
Sequential Function Chart (SFC) - the "everything" language
To read more about these, you can read here.
If you want to play around with a PLC Simulator, they are incredibly expensive, but there are several free simulation solutions out there. Do-More Designer is one of them.
One of the common languages is PLC ladder logic. In ladder logic, the control logic is written from top to bottom, hence making it look like a ladder with each step being called a Rung.
The control logic program is executed form left to right of each rung. Once a rung is executed, it moves to the lower rung from top to bottom.
For more knowledge about what a PLC is, there is a short 1 minute video giving an example:
Or a longer 6 minute video for even more detail:
Some advantages of a PLC include:
Reliability
Versatility and flexibility
Simple installation and troubleshooting
Quick modification through changing the code/program
Small footprint
Low power consumption
High processing speed
As with all things, there are disadvantages. Some of these include:
Expensive initial cost
Highly specialized repair
Non uniform programming language
Prone to vulnerability and cyber attacks as it has software and not purely mechanical
At this point, why are we discussing PLC? What is its relevance to cyber security as this website is all about? Well, the PLC designers were not cybersecurity experts to implement security. Many of the PLC devices are old (legacy devices) and at the time of their development, there were no security concerns.
Many of the PLC devices were not connected to the network. However, nowadays, recent protocols connect PLCs to networks for remote monitoring and management.
An example is LOGO! which is a PLC manufactured by Siemens. It has three vulnerabilities that could allow remote attackers to reconfigured the device, access project files, decrypt files, and access passwords.0
Ok, time to move on to other components!
Remote Terminal Unit (RTU)
Similiar to a PLC, it is a microcontroller that performs the logic for controlling the machines and processes. RTUs are the boundary between the cyber world and the real world controlling physical processes.
RTUs are developed with similiar capabilities as PLCs.
They originally had proprietary programming languages, but are now switching to the same PLC standard languages.
Intelligent Electronic Device (IED)
An IED is once again very similiar to PLCs and RTUs. It is a microcontroller that performs the logic for controlling the machines and processes. They provide a visual display and operator controls on the device front panel.
IED provide protective control, communication and monitoring functionalities. Digital Protective Relays are essentially IEDs.
IED protection could include detecting faults as a substation such as over-current, earth faults, phase discontinuity, as well as over and under voltage conditions.
Engineering Workstation (EWS)
An EWS is a desktop computer or server running a standard OS such as Windows or Linux. This machine hosts the programming software for the controllers (PLC, RTU, IED) and applications.
Engineers use this platform to make changes to controller logic and industrial applications, the automation process logic is adjusted and deployed to controllers from this machine.
Human Machine Interface (HMI)
HMI is a software application. It monitors multiple processes and provides situational awareness of the automation processes to the operator such as:
Values
Alarms
Data Trends
It can be programmed with the capability for the operator to send commands to a controller. HMI can offer controls which the plant operator can use to manually control plant components such as opening or closing vales and starting or stopping pumps.
Data Historian
A data historian or operational historian collects real-time process data from automation processes and aggregates them in a database for concurrent and later analysis.
Data which is displayed by HMI is stored in the historian and each data point is timestamped. It may have interfaces with industrial protocols such as Modbus or Open Platform Communications (OPC) to directly connect to a HMI, PLC or RTU to retrieve data.
Communication Gateways
A communication gateway enables two devices with dissimilar protocols or transport to communicate.
An example of this transformation is the translation from Modbus messages on a serial link or RS-232/RS-485 to OPC messages on Ethernet.
Front End Processors
FEP is a dedicated communications processor. FEP is used when an HMI or control center server needs to poll status information from multiple RTUs or IEDs.
FEP may include Communications gateway functions such as converting from vendor proprietary protocols to open standard ones.
ICS Field Devices
Field devices are the sensors, transducers, actuators, and machinery which directly interface with a controller (PLC, RTU, or IED) via the digital or analog I/O module. They may use an industrial protocol such as Modbus or PROFIBUS to communicate with the controller.
They could be sensors that measure temperature, humidity, pressure, sound, vibration, voltage and current as well as other physical characteristics.
They could be actuators performing a task such as valve controllers, motor controllers, frequency converters, and solenoids which are controlling motors, pumps, valves, turbines, agitators, burners and compressors.
Types of ICS
ICS are characterized according to their use as well as the geographic separation between the controller (PLC, RTU, IED) and the supervisory components such as the HMI and Data Historian.
Process Control System
Safety Instrumented System
Distributed Control System
Building Automation System
Supervisory Control and Data Acquisition System
Energy Management System
Process Control System (PCS)
A PCS controls an automation process in a manufacturing environment.
Safety Instrumented System (SIS)
These take actions to prevent an unsafe plant state or operation. SIS has sensors sending input signals to a controller which is programmed to actuate equipment to prevent an unsafe state or mitigate the impact of unsafe operations.
SIS is a process separate from a PCS. SIS drives the system towards a safe state when there is an unsafe state that can present a risk to the plant, personnel or general public. A simple example of an unsafe plant state is the flame-out of an incenerator which could result in accumulation of fuel gas.
The SIS should be completely - in practice - separated from the PCS and they are just in place not for controlling purposes, but rather provide safety in the circumstance of a disaster.
Distributed Control System (DCS)
These are systems that control multiple automation processes at a single site (or plant). A DCS may monitor and supervise several PCSs at a plant.
Your ICS could be distributed (controlling multiple factories/plants/PCS) and this type of a system is called a DCS. Another example is a power plant as shown near the start.
Building Automation System (BAS)
A BAS is a type of ICS which monitors and controls a buildings infrastructure services such as heating, ventilation, air conditioning, and cooling (HVAC), lighting, sunshields, elevators, fire protection, energy management and security.
Supervisory Control and Data Acquisition System (SCADA)
These collect data and monitors automation across geographical areas. SCADA control centres monitor, manage and control remote field controllers such as RTUs and IEDs and provides this info to operators using the HMI.
They may supervise one or more DCSs or PCSs. DCSs and PCSs are near the machinery under-control and they frequently poll the PLCs status info each second. The SCADA control center could be separated from RTUs by thousands of miles and may poll the controllers less frequently than a DCS or PCS.
The SCADA is NOT in the field zone often. The PLCs are usually in the field zone and they capture the data from the sensors/actuators frequently. This data is then accumulated - often in the PLCs - and every now and then transmitted to the SCADA systems.
SCADA is a system architecture comprising computers networked data communications and graphical user interfaces for high-level supervision of machines and processes.
Energy Management System (EMS)
These monitor and control the generation and transmission of electricity. This is a type of SCADA system that manages the power grid nationally and even internationally.
Midcontinent Independent System Operator (MISO) is an EMS covering 65,800 miles of transmission lines between US and Canada.