Anonymous - TryHackMe Writeup
The link for this lab is located here: https://tryhackme.com/room/anonymous
This is a virtual machine meant for beginners. Acquiring both flags will require some basic knowledge of Linux and privilege escalation methods.
Full Walkthrough
The first step is to scan the machine across all ports using Nmap with the following parameters:
-p- for all ports
10.10.39.146 for the target IP
-oN allports.scan to output in Nmap format.
This reveals 4 ports open - FTP, SSH, and SMB (ports 139 and 445). With this information, it’s a good idea to start enumerating the services more by first performing a more detailed scan on the specified ports.
We get a ton of information back including anonymous FTP login is allowed, VSFTPd 2.0.8 or later, and some various SMB information. We can start by enumerating the FTP share by logging in using anonymous:anonymous as the credentials.
Listing out the contents of the directory reveals a “scripts” folder - let’s look inside.
This reveals a couple of interesting things including what looks like a script. We can download all the files using the following command:
mget *
Firstly, we can look at the to_do.txt file to see what tasks need to be done. This reveals that it’s simply a note for the admin to disable anonymous login.
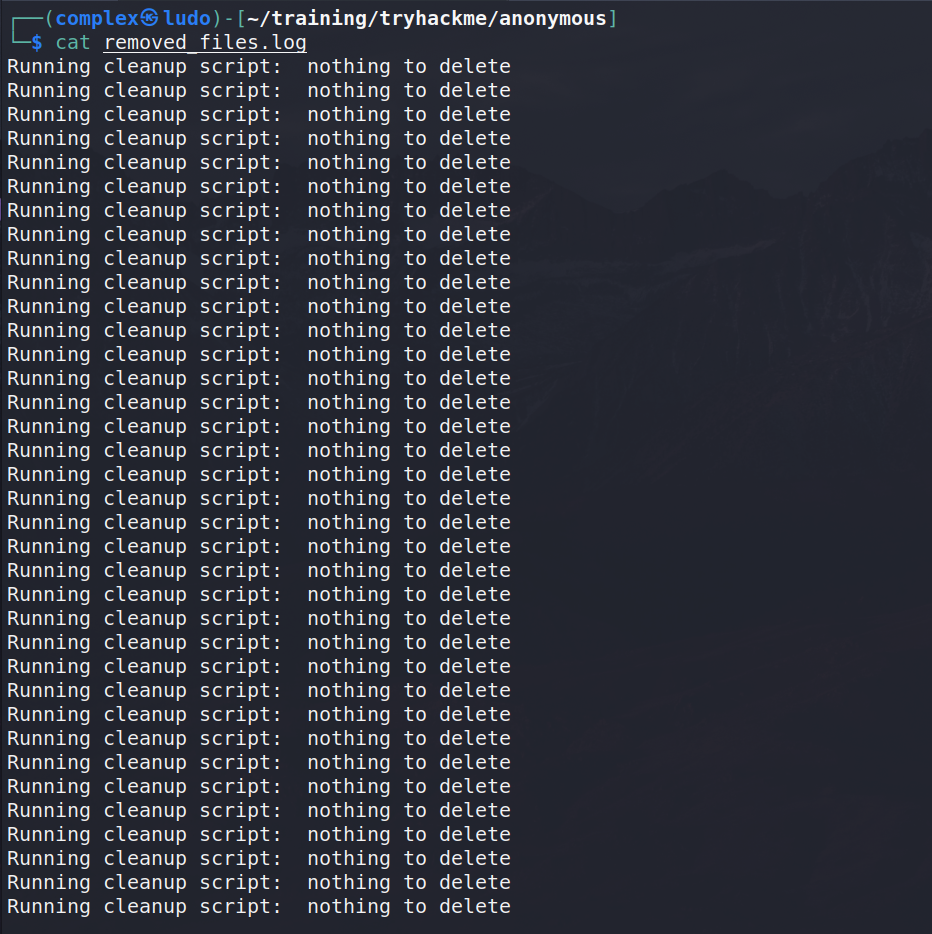
Next, we can read the log - it simply contains the following line that indicates it is running a cleanup script.
Finally, the most important file - clean.sh. This file seems to iterate through a directory and remove any files.
Initially, in this bash script, the variable “tmp_files” is set as 0.
In the if check, the script checks whether value of tmp_files is equal to 0. If so, it echoes a message like: “Running cleanup script: nothing to delete” into “removed_files.log” file. Now that’s interesting. Because; if we look on the removed_files.log file, maybe we can get some valuable information.
Lastly, in else condition, if the value of tmp_files is other than 0, it removes the file and prints another message
Since this file is in the FTP directory, we can try overwriting it with a BASH reverse shell one-liner like the following below:
Then, we start a Netcat listener on the same port - in my case, port 7777.
Finally, we can try reconnecting to the FTP service and try uploading our modified “clean.sh” script up to the share.
In the case of this, since it’s outputting a ton to a log file, it might be running on a schedule via a cron job. Testing this theory we can wait a little bit to see if it runs automatically - if not, we can move on and enumerate other services like SMB.
Fortunately for us, it returns a shell about 2 minutes later.
With this shell, we can stabilize the shell using Python3 and then try to get an easy win by checking our sudo permissions - but we don’t have any and we can’t provide a password either.
Enumerating further, we list the contents of the current directory and can grab the user.txt flag for submission.
For further enumeration, we can use LinPEAS. To start, we utilize a Python3 server to serve the linpeas.sh file up.
Then, on the target machine, we can use the wget command to download linpeas.sh to the /tmp folder since it’s world writable.
Finally, we can run the script.
After a few minutes, we can scrape through the results. Something critical is highlighted under the SUID section - the /usr/bin/env command has SUID permissions set.
Going to ye old faithful GTFOBins and see if there is something we can do with env regarding SUID permissions.
And there is! With /usr/bin/env, we can use it to execute /bin/bash with root permissions and grab a root shell.